Audio watermarking embeds hidden data directly into audio files, while audio fingerprinting extracts unique patterns from the audio without altering it. Both are used to protect and identify digital audio, but they serve different purposes:
- Watermarking is ideal for proving ownership and tracking distribution. It embeds data into the audio signal, making it resilient to playback and conversions but vulnerable to compression and distortion.
- Fingerprinting identifies audio by matching it to a database. It doesn’t modify the file, works well with noisy or compressed audio, but requires a database and internet connection.
Key Differences:
- Watermarking embeds data into the file; Fingerprinting analyzes the audio as-is.
- Watermarking works offline; Fingerprinting relies on a database.
- Watermarking is better for tracking leaks; Fingerprinting excels in content identification.
A combined approach offers stronger protection: watermarking tracks the source, while fingerprinting identifies the content.
Stopping Piracy and Deepfakes at Once
What is Audio Watermarking?
Audio watermarking embeds hidden digital data directly into an audio file. Unlike metadata, which can be easily removed, a watermark integrates into the audio signal itself, making it a lasting tool for proving ownership, tracking distribution, and safeguarding intellectual property.
The key feature of audio watermarking is its perceptual transparency – listeners can’t detect the embedded data. As researcher Sanjay Pratap Singh Chauhan explains:
"Digital audio watermarking technique is a process of embedding perceptually transparent digital information into an original audio signal" [1].
This embedded data remains intact through playback, file conversions, and even re-recordings, ensuring it stays with the audio throughout its entire lifecycle. Below, we’ll explore how this process works and why it’s both effective and discreet.
How Audio Watermarking Works
Watermark embedding involves analyzing audio in either the time domain or transform domains, such as Discrete Wavelet Transform (DWT) or Discrete Cosine Transform (DCT). About 60% of current watermarking research focuses on the wavelet domain, as it strikes a balance between being robust and staying imperceptible [2].
Some common embedding techniques include:
- Quantization Index Modulation (QIM): Adjusts the audio signal by quantizing it differently for binary "0" and "1" bits.
- Least Significant Bit (LSB) Insertion: Hides data in the least significant bits of audio samples.
- Echo Hiding: Adds faint echoes to the audio, which the human brain perceives as part of the original sound due to the Haas effect [4].
To ensure the watermark remains inaudible, psychoacoustic modeling places it in frequency ranges that are less sensitive to human hearing. This maintains a signal-to-watermark power ratio of about 20 dB [3]. Carlos Jair Santin-Cruz, a Ph.D. candidate, highlights the importance of this balance:
"The watermark should be imperceptible; if the watermark is noticeable, this can be annoying or even make the host signal unintelligible" [2].
Most watermarking algorithms – about 90% – are "blind", meaning they allow data recovery without needing the original file [2]. This ensures that verification is possible even if the source file is unavailable.
Benefits of Audio Watermarking
Watermarking provides a reliable way to protect and manage audio content. Here’s how:
- Proof of Ownership: Unlike metadata, a watermark is permanent and remains embedded in the file through downloads, uploads, and format changes. This makes it a solid tool for resolving copyright disputes.
- Forensic Tracking: Streaming platforms can use unique watermarks for each user or distribution channel. This "transactional watermarking" helps trace the source of leaked or unauthorized content.
- Automated Monitoring: Watermarks enable automated systems to monitor broadcasts for royalty payments, trigger second-screen services, or manage content access without manual effort.
Drawbacks of Audio Watermarking
The biggest challenge lies in balancing imperceptibility, robustness, and capacity – a dilemma often referred to as the "Magic Triangle" [2]. Enhancing one factor usually compromises another.
Lossy compression is a particular hurdle. Formats like MP3 are designed to eliminate inaudible data, which is exactly where watermarks are hidden. Daniel Jones, Chief Science Officer at Chirp, explains:
"The crux of watermarking is that it should be done in a way that is (a) imperceptible to the listener, yet (b) be resilient to distortion and compression" [4].
Techniques like resampling, filtering, and time-stretching can also degrade or erase watermarks, leading to detection errors [3]. This makes it essential to continually refine watermarking methods to withstand these challenges.
What is Audio Fingerprinting?
Audio fingerprinting takes a completely different approach from watermarking. Instead of embedding extra data into an audio file, it extracts a unique digital signature based on the audio’s existing features. This signature acts like a "fingerprint", capturing the essence of the sound without altering the file itself.
The key advantage here is that fingerprinting leaves the original audio untouched. As Daniel Jones, Chief Science Officer at Chirp, explains:
"The greatest power – and the greatest constraint – of fingerprinting is that it does not modify the original source material in any way" [4].
Because it’s non-destructive, you can create a fingerprint for any audio file without needing to process or modify it beforehand. The technology analyzes the audio as it is and generates a compact "digest" summarizing its unique, perceptually important features [3][4]. This fingerprint is then compared against a large database to identify the track. A well-known example of this is Shazam, which uses its database of tens of millions of tracks to identify songs from short, even noisy, audio clips [4].
How Audio Fingerprinting Works
The process behind audio fingerprinting involves analyzing features of the audio that remain consistent across different conditions. For example, it extracts characteristics like:
- Mel-Frequency Cepstral Coefficients (MFCC), which mimic how humans perceive sound.
- Chromagrams, which capture pitch and harmonic patterns.
- Spectral contrast, which highlights energy differences across frequencies [5].
These features are combined into a mathematical representation that’s highly resilient to distortions. Whether the audio is compressed, played through a low-quality speaker, or has background noise, the fingerprint remains recognizable.
Matching fingerprints involves comparing the extracted signature to a reference database using similarity measures like Cosine similarity or Dynamic Time Warping. A 2025 study introduced the HashWave framework, which achieved a True Positive Rate of 0.952 with just a 1% False Positive Rate, even after testing across more than 20 different audio transformations [5]. Impressively, this matching process operates with sub-second latency on a single CPU node [5].
Benefits of Audio Fingerprinting
Audio fingerprinting stands out for its ability to identify content across a wide range of audio qualities. Unlike watermarking, which can be fragile under compression or filtering, fingerprinting analyzes the entire audio signal, making it naturally more resilient to distortions [3][4].
It’s also format-agnostic, meaning it works with any audio file type. This makes it an excellent tool for monitoring broadcasts or streaming platforms. For instance, Nielsen Broadcast Data Systems uses fingerprinting to scan radio stations worldwide, ensuring that rights holders are properly compensated by identifying copyrighted material in broadcast streams [4].
Another advantage is its ability to process existing audio collections immediately, without requiring any prior modifications to the files.
Drawbacks of Audio Fingerprinting
The biggest challenge with audio fingerprinting is its reliance on a reference database. It can only identify audio that already exists in the database [4].
This dependency leads to two practical issues. First, you typically need an internet connection to access the database, whereas watermarking can often be decoded offline [4]. Second, fingerprinting doesn’t allow for embedding additional data, such as transaction IDs or real-time updates like live sports scores [4].
Another drawback is the computational effort required to search through massive databases. As libraries grow to include tens of millions of tracks, scaling becomes more difficult. Additionally, high levels of background noise can significantly impact detection accuracy [3].
Audio Watermarking vs. Audio Fingerprinting: Main Differences
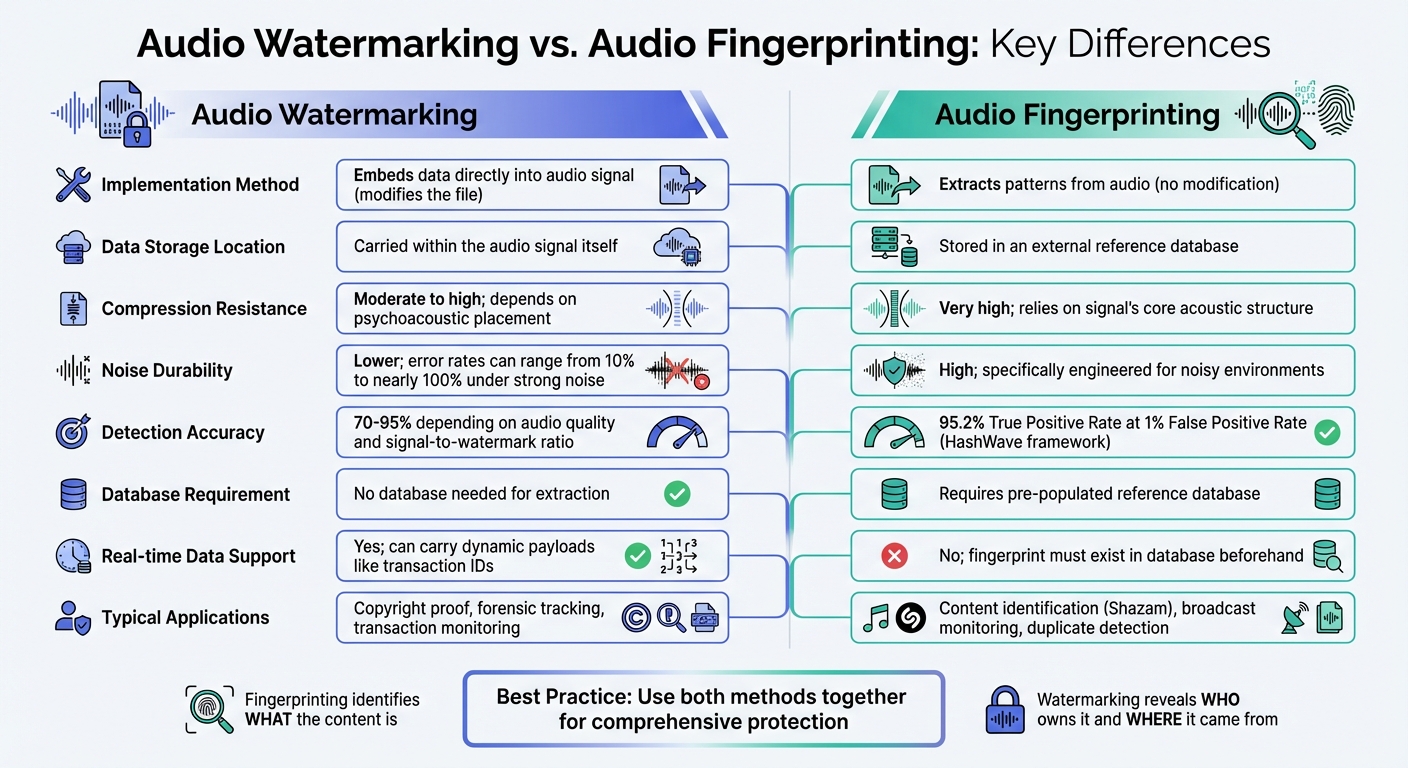
Audio Watermarking vs Audio Fingerprinting: Key Differences Comparison
The key distinction between audio watermarking and audio fingerprinting lies in how they function. Watermarking actively embeds data into the audio signal, altering the file in the process, while fingerprinting passively extracts unique patterns from the audio without modifying it [2][4].
This core difference influences how each method operates. Watermarking stores its data directly within the audio file, enabling information retrieval without needing an external database [4]. On the other hand, fingerprinting generates a unique "signature" for the audio, which has to be matched against an external database to retrieve metadata [4][3]. As Daniel Jones, Chief Science Officer at Chirp, explains:
"The crux of watermarking is that it should be done in a way that is (a) imperceptible to the listener, yet (b) be resilient to distortion and compression" [4].
These differences also affect their resilience to compression. Fingerprinting generally performs better in this area because it analyzes the underlying structure of the audio signal, allowing it to withstand lossy compression formats like MP3 [3][4]. Watermarking, however, can struggle with compression, as lossy codecs often remove the frequency ranges where watermarks are embedded [4]. This contrast shapes how streaming services and other platforms choose between these technologies.
Comparison Table
Here’s a quick breakdown of their main differences:
| Aspect | Audio Watermarking | Audio Fingerprinting |
|---|---|---|
| Implementation Method | Embeds data directly into audio signal (modifies the file) [2][4] | Extracts patterns from audio (no modification) [4][3] |
| Data Storage Location | Carried within the audio signal itself [4] | Stored in an external reference database [4] |
| Compression Resistance | Moderate to high; depends on psychoacoustic placement [4] | Very high; relies on signal’s core acoustic structure [3][4] |
| Noise Durability | Lower; error rates can range from 10% to nearly 100% under strong noise [3] | High; specifically engineered for noisy environments [4] |
| Detection Accuracy | 70-95% depending on audio quality and signal-to-watermark ratio [3] | True Positive Rate of 95.2% at 1% False Positive Rate (HashWave framework) [5] |
| Database Requirement | No database needed for extraction [4] | Requires pre-populated reference database [4][3] |
| Real-time Data Support | Yes; can carry dynamic payloads like transaction IDs [4] | No; fingerprint must exist in database beforehand [4] |
| Typical Applications | Copyright proof, forensic tracking, transaction monitoring [2][4] | Content identification (Shazam), broadcast monitoring, duplicate detection [3][4] |
sbb-itb-738ac1e
How Streaming Platforms Use These Technologies
Streaming platforms rely on both audio watermarking and fingerprinting to address different challenges in content protection. Watermarking is primarily used to trace leaks, while fingerprinting helps identify unauthorized content. Here’s a closer look at how each technology plays a role in safeguarding and monitoring digital audio content.
Audio Watermarking Applications
Watermarking is a go-to tool for streaming services when it comes to forensic tracking and live-stream protection. Using "transactional watermarking", platforms embed unique identifiers into each stream, creating distinct copies for individual users. If pirated content surfaces online, this method allows platforms to trace the leak back to the specific user account or session responsible for the breach [6].
For live-streamed events, real-time watermarking is critical. These systems embed imperceptible data into the content as it is being streamed, all while maintaining ultra-low latency to ensure a smooth viewing experience. To keep the watermark undetectable, the systems typically maintain a signal-to-noise ratio (SNR) of at least 20 dB [7].
Watermarking also supports second-screen applications by embedding sync data directly into the audio. This enables interactive features on viewers’ mobile devices in real time, without needing an internet connection for precise timing [4][2]. As Daniel Jones, Chief Science Officer at Chirp, explains:
"A watermark for copyright control should be as difficult as possible to detect and remove from the original broadcast, and ideally use cryptographic processes that can not easily be reverse-engineered" [4].
Audio Fingerprinting Applications
Unlike watermarking, which embeds traceable data into audio, fingerprinting focuses on identifying content in a non-invasive way.
Fingerprinting is a powerful tool for recognizing content and tracking royalties across massive audio libraries. Streaming platforms use it to automatically detect copyrighted music in user-generated content, even if the audio has been compressed, mixed with dialogue, or played in the background [8]. This capability extends to identifying unmarked content, allowing platforms to scan older archives for new tracks [9].
In the realm of broadcast monitoring and royalty management, fingerprinting scans thousands of radio and TV streams to ensure rights holders are properly compensated [4]. Premium platforms also use it to monitor the web for pirated clips, including those shared on Telegram or Reddit. Even when these clips are cropped or altered to bypass other protections, fingerprinting can still identify them [8].
Additionally, fingerprinting helps manage large media libraries by identifying duplicates and cataloging assets without altering the original files. This non-destructive approach ensures audio quality remains intact while providing robust identification, even for heavily edited or noisy content [8].
Choosing Between Audio Watermarking and Fingerprinting
Watermarking and fingerprinting serve different purposes: watermarking tracks individual copies, while fingerprinting identifies the content itself. Your choice depends on the specific protection needs of your project.
Decision Factors
The first thing to consider is whether you’re okay with modifying your audio files. Fingerprinting doesn’t alter the original audio, making it a great choice for tasks like broadcast monitoring or identifying songs in noisy environments. As Daniel Jones, Chief Science Officer at Chirp, explains:
"The greatest power – and the greatest constraint – of fingerprinting is that it does not modify the original source material in any way" [4].
Watermarking, however, embeds data directly into the audio signal. This change is typically subtle and undetectable to listeners, but it does modify the file.
Infrastructure needs also differ. Fingerprinting relies on a pre-built database and requires significant processing power. In contrast, watermarking can work offline and doesn’t need external resources. If you’re dealing with live streams or need real-time tracking without database lookups, watermarking provides a faster, localized solution.
Budget and resources are another key consideration. Watermarking demands less computational power but is less effective in noisy conditions. Fingerprinting, on the other hand, requires robust database support and heavy processing but performs well even in challenging environments.
Using Both Methods Together
Combining watermarking and fingerprinting can create a more comprehensive protection strategy. Fingerprinting excels at identifying content, while watermarking pinpoints its source. Together, they offer a layered defense.
This dual approach is particularly useful if watermarks are removed. Even if attackers strip out the embedded data, fingerprinting can still identify the content. Meanwhile, watermarks can provide critical forensic details, like user IDs or transaction codes, that fingerprinting alone can’t deliver.
How ScoreDetect Protects Audio Content
With digital piracy constantly evolving, ScoreDetect steps in as a robust solution for safeguarding audio content. By combining imperceptible watermarking, blockchain timestamping, and AI-powered monitoring, it creates a multi-layered defense system. This approach addresses the shortcomings of traditional methods, making it harder for pirates to steal or distribute unauthorized content.
ScoreDetect Features
ScoreDetect uses invisible watermarks embedded directly into audio files. These watermarks act as a permanent marker of ownership and remain intact even after MP3 compression, pitch shifting, or time stretching. Research shows that these watermarks stay undetectable, even under signal-processing attacks [1]. With an embedding capacity of 20 bits per second, the system ensures effective tracking [7].
Blockchain timestamping adds another layer of security. By recording a checksum of the audio content on the Ethereum blockchain, it creates a tamper-proof ownership record. This method doesn’t store the actual audio files, only the cryptographic proof of their creation. Impressively, the average contract time for this process is just 0.044 seconds [5].
The platform also leverages AI-powered monitoring to detect unauthorized use. Its web scraping technology bypasses 95% of anti-scraping measures, scanning streaming platforms, IPTV services, and social media for pirated content. Once detected, it issues automated takedown notices with a success rate of over 96%.
Together, these features offer a powerful toolkit for combating piracy.
Benefits for Streaming Platforms
Streaming platforms often deal with issues like stream ripping, metadata tampering, and unauthorized sharing. ScoreDetect’s layered approach tackles these challenges head-on. Its watermarking and blockchain verification provide court-admissible evidence, making it easier to trace leaks back to their source [10]. This is especially useful for identifying pre-release leaks or pinpointing accounts responsible for illegal distribution.
Additionally, ScoreDetect’s integration with over 6,000 web apps through Zapier allows streaming platforms to automate their response to piracy. Automated workflows triggered by detected violations reduce the need for manual intervention, saving time and resources while enhancing overall security.
Conclusion
Audio watermarking and audio fingerprinting serve distinct yet complementary purposes in content protection. Watermarking embeds hidden ownership data directly into files, while fingerprinting identifies unique characteristics of audio without altering the source. As Daniel Jones, Chief Science Officer at Chirp, puts it:
"The greatest power – and the greatest constraint – of fingerprinting is that it does not modify the original source material in any way" [4].
Watermarking works proactively by embedding traceable information before content is distributed, making it effective for forensic tracking, such as pinpointing which user leaked a file. On the other hand, fingerprinting is reactive, excelling at high-volume tasks like identifying user-generated content or monitoring broadcasts for royalty purposes.
For streaming platforms in a media market expected to surpass $120 billion, relying solely on one method leaves gaps in protection [11]. A combined approach is far more robust: fingerprinting determines what the content is, while watermarking uncovers who owns it and where it came from. By leveraging both technologies, platforms can achieve stronger security.
ScoreDetect offers a comprehensive solution by integrating invisible watermarking, blockchain timestamping, and AI-driven monitoring. Its watermarks resist signal-processing attacks, while its web scraping tools locate pirated content with a 95% bypass rate. Additionally, automated takedown notices boast an impressive 96% success rate, ensuring thorough protection for audio content.
FAQs
How does audio watermarking stay intact during playback and file conversions?
Audio watermarking is crafted to stay embedded in audio files, even when they’re played, compressed, or converted into other formats. This is made possible through advanced methods like spread-spectrum encoding and transform domain techniques, which integrate the watermark in a way that resists typical alterations like compression, trimming, or format changes.
These methods ensure the watermark remains hidden from listeners but detectable by specialized tools, even after the audio is modified. This durability makes audio watermarking a dependable way to safeguard digital content across different platforms.
What challenges does audio fingerprinting face when identifying new or unregistered audio content?
Audio fingerprinting faces challenges when it comes to identifying new or unregistered audio. The system relies on a database of pre-existing fingerprints, so if a piece of audio hasn’t been cataloged or registered before, it won’t be able to recognize or match it.
This makes fingerprinting less effective for spotting unauthorized use of newly created or unlisted content, as there’s no existing reference for comparison.
Can audio watermarking and fingerprinting work together to improve audio security?
Yes, audio watermarking and audio fingerprinting work well together to strengthen audio security. Here’s how they differ and complement each other:
- Audio watermarking embeds subtle, hard-to-detect markers directly into the audio file. These markers can verify ownership or trace unauthorized use.
- Audio fingerprinting analyzes the unique characteristics of an audio file to identify and match it without altering the original content.
By combining these two techniques, you can create a stronger defense for digital audio. Watermarking is ideal for proving ownership, while fingerprinting shines in detecting unauthorized sharing or usage across platforms. Together, they form a powerful strategy to combat piracy and manage digital audio assets.

