Navigating cross-border digital compliance can be overwhelming, but it’s non-negotiable for businesses operating internationally. Non-compliance risks include hefty fines – up to 6% of global revenue under the EU’s Digital Services Act or £18 million under the UK’s Online Safety Act. Here’s what you need to know:
- Key Regulations: GDPR (EU/UK), CCPA/CPRA (US), and new laws like the Digital Services Act (EU) and Online Safety Act (UK) impose strict rules on data privacy, content moderation, and user safety.
- Global Trends: Emerging laws in countries like India, South Korea, and Canada are expanding regulatory oversight, often with cross-border implications.
- Compliance Tools: AI and blockchain are transforming compliance by automating monitoring, data protection, and intellectual property management.
- Strategies: Centralized compliance frameworks, robust vendor screening, and real-time auditing are essential for managing risks.
Compliance is no longer just about avoiding penalties; it builds trust and ensures market access. The right tools and strategies can help your business stay ahead in this complex landscape.
Cross-Border Data Transfer Regulations and Compliance Requirements | Exclusive Lesson
Key International Compliance Frameworks
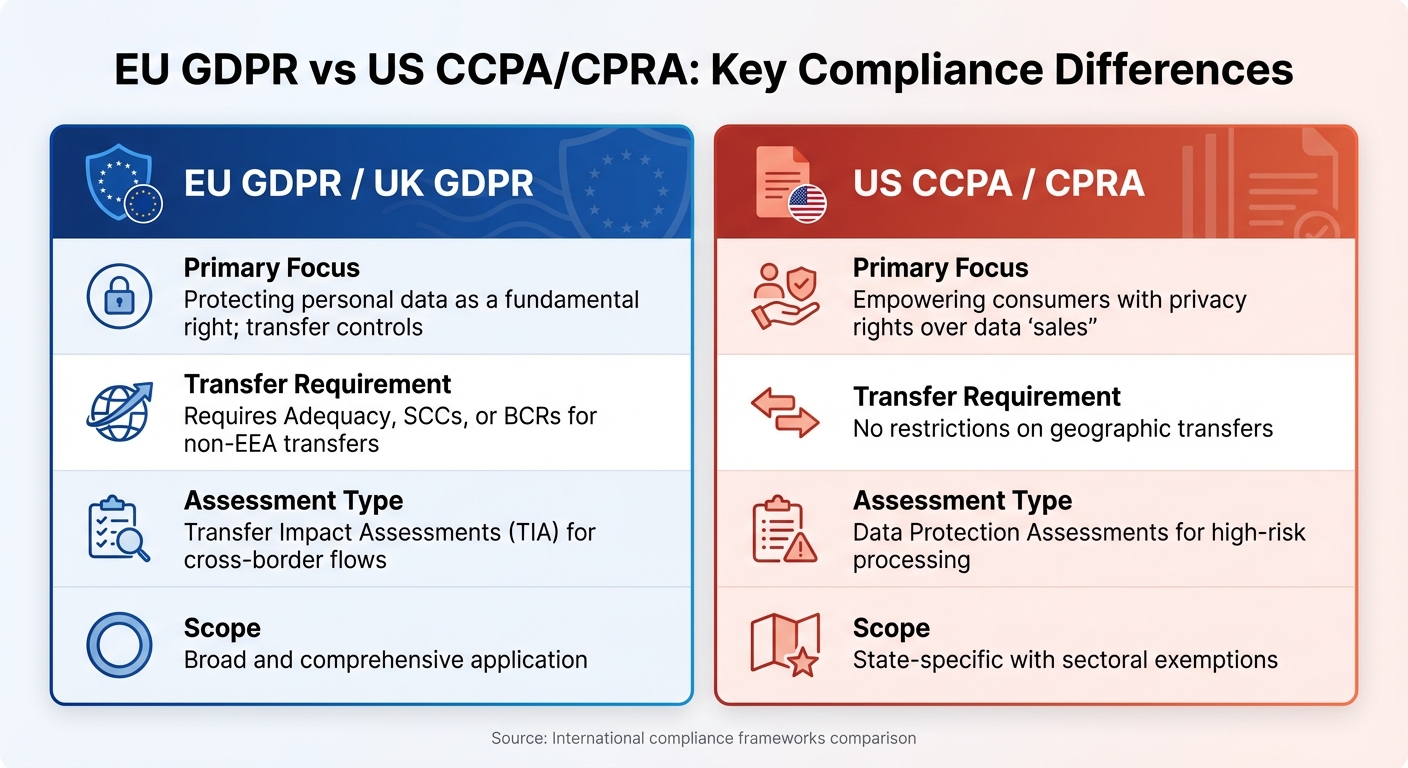
EU GDPR vs US CCPA/CPRA: Key Compliance Differences
International regulations play a crucial role in shaping how organizations handle data, ensure privacy, and manage digital content.
EU GDPR and Data Protection Rules
The General Data Protection Regulation (GDPR) sets a benchmark for protecting personal data across the European Economic Area (EEA). If your business processes data belonging to EU residents, compliance is mandatory – no matter where you’re located.
"The GDPR aims to guarantee an equivalent level of protection to personal data being transferred to the one they enjoy within the EEA." – European Data Protection Board [4]
Under GDPR, transferring personal data outside the EEA is restricted unless specific conditions are met. These include an adequacy decision (where the destination country is deemed to provide sufficient protection) or the use of appropriate safeguards like Standard Contractual Clauses (SCCs) or Binding Corporate Rules (BCRs). The European Commission updated these safeguards in June 2021 [4].
Organizations must also conduct a Transfer Impact Assessment (TIA) to ensure that the destination country’s laws don’t compromise data protection. If gaps exist, additional measures, such as encryption, are necessary [4]. The Schrems II ruling highlighted that adequacy decisions alone may not always suffice, prompting companies to reassess their data transfer practices [4].
The UK introduced an extension to the EU-US Data Privacy Framework on October 12, 2023, permitting "adequate" data transfers to U.S. organizations participating in the framework [5]. However, adequacy decisions can be revoked, so ongoing monitoring is essential [4].
US CCPA/CPRA and Federal Trade Commission Guidelines
The United States approaches data privacy differently, relying on a patchwork of state laws and sector-specific regulations instead of a unified federal framework. Leading the charge is California, with its California Consumer Privacy Act (CCPA) and the updated California Privacy Rights Act (CPRA), which prioritize consumer rights over personal data [1].
Unlike the GDPR, which emphasizes cross-border data transfer restrictions, the CCPA/CPRA grants consumers the right to access, delete, correct, and restrict the sale or sharing of their data [1]. Businesses must identify data flows that qualify as a "sale" or "sharing" under these laws and provide opt-out mechanisms [1].
State laws often include sectoral exemptions for industries regulated by federal laws, such as HIPAA for healthcare and GLBA for financial services. In contrast, GDPR applies more uniformly across sectors [1]. On the federal level, the Federal Trade Commission (FTC) enforces compliance, increasingly scrutinizing "dark patterns", addictive app designs, and algorithmic manipulation [1].
| Feature | EU GDPR / UK GDPR | US CCPA / CPRA |
|---|---|---|
| Primary Focus | Protecting personal data as a fundamental right; transfer controls [4] | Empowering consumers with privacy rights over data "sales" [1] |
| Transfer Requirement | Requires Adequacy, SCCs, or BCRs for non-EEA transfers [4] | No restrictions on geographic transfers [1] |
| Assessment Type | Transfer Impact Assessments (TIA) for cross-border flows [4] | Data Protection Assessments for high-risk processing [1] |
| Scope | Broad and comprehensive application [4] | State-specific with sectoral exemptions [1] |
Emerging Global Standards
New frameworks are reshaping global compliance beyond GDPR and CCPA. The EU Digital Services Act (DSA), which becomes fully operational in 2025, imposes obligations on Very Large Online Platforms (VLOPs) to conduct risk assessments and moderate content. Non-compliance can result in fines of up to 6% of global annual turnover [1]. Similarly, the UK’s Online Safety Act (OSA), effective March 2025, applies to around 100,000 digital services, with penalties reaching £18 million or 10% of global revenue, whichever is higher [1].
Algorithmic transparency is also gaining momentum worldwide. For instance, South Korea’s "Basic Act on the Development of Artificial Intelligence and Creation of a Trust Base" mandates disclosure of how recommender systems operate and measures to prevent algorithmic bias [1]. Japan is making parallel updates to its Act on the Protection of Personal Information (APPI) [1].
Other noteworthy developments include:
- India’s Digital India Act: A replacement for the Information Technology Act 2000, introducing stricter intermediary liability rules [1].
- Canada’s Online Harms Act: Focused on platform accountability for misinformation and child safety [1].
- Malaysia’s Online Safety Act: Passed in December 2024 and effective in 2025, requiring safety plans and distinguishing between "harmful" and "priority harmful" content [1].
The UK’s Crime and Policing Bill, introduced in February 2025, adds another layer of accountability. Platforms must appoint "content managers" who are personally liable for removing illegal content within 48 hours of notice, with fines as high as £10,000 [1].
These emerging regulations highlight a growing trend toward extraterritorial reach. Laws increasingly apply to platforms serving local users, regardless of where a company is headquartered. As compliance requirements evolve, businesses must adopt strategic approaches to navigate this complex global landscape.
Strategies for Achieving Cross-Border Compliance
Navigating cross-border compliance isn’t just about following rules – it’s about building systems that manage data flows, monitor operations, and verify ownership effectively.
Managing Data Transfers with Technology
Transferring data across borders requires careful adherence to legal frameworks. Under UK GDPR, a restricted transfer happens when personal data is sent to a recipient outside the UK who acts as a separate controller or processor [5]. Transfers to countries with adequacy decisions – like the EEA, Gibraltar, and South Korea – are straightforward. However, transfers to other regions require safeguards such as the International Data Transfer Agreement (IDTA), the UK Addendum to EU Standard Contractual Clauses (SCCs), or Binding Corporate Rules (BCRs), along with a Transfer Risk Assessment (TRA) [5].
A TRA ensures that the destination country’s laws won’t undermine data protection standards. The Information Commissioner’s Office emphasizes:
"People risk losing the protection of the UK data protection laws if their personal data is transferred outside the UK" [5].
To streamline compliance efforts across multiple jurisdictions, businesses often use centralized dashboards. These tools track critical filings – like financial statements, tax reports, and sector-specific documentation – for all operating regions [3].
Many global organizations adopt a hub-and-spoke model: a central team sets policies and oversees compliance, while local teams handle region-specific requirements [3]. Combining this model with AI-powered monitoring can significantly enhance real-time compliance efforts.
Using AI for Compliance Monitoring
Artificial intelligence has shifted compliance monitoring from reactive to proactive. AI systems can scan global markets, social platforms, and websites for counterfeit or pirated content, generating real-time alerts to prevent breaches. These tools automate the discovery, classification, and analysis of critical information, allowing businesses to manage vast digital footprints without constant manual effort.
For cross-border payment systems, AI identifies and flags suspicious patterns across different markets, reducing the need for manual oversight. This frees up staff to focus on more complex, judgment-based tasks instead of repetitive monitoring.
AI also plays a critical role in meeting new content moderation regulations. For example, under the UK’s Online Safety Act, platforms must identify "priority harmful content", a requirement that impacts an estimated 100,000 digital services [1]. AI-driven tools can scan for unusual activity, issuing alerts to stop data breaches or fraud before they escalate globally.
Organizations handling sensitive information – like financial institutions, healthcare providers, and government agencies – benefit significantly from AI’s efficiency. Tools like ScoreDetect leverage advanced AI to uncover unauthorized content with a 95% success rate, analyzing and matching findings to provide quantitative proof of misuse. This level of automation not only enhances security but also reduces costs compared to manual monitoring.
Paired with AI’s real-time capabilities, blockchain technology offers another layer of security by providing immutable proof of ownership.
Using Blockchain for Proof of Ownership
Blockchain technology creates secure, timestamped records of digital assets using checksums – unique digital fingerprints. These records serve as globally recognized proof of ownership without storing the actual content. This approach addresses a major challenge in cross-border operations: establishing ownership across decentralized internet platforms and varying legal systems [2]. While Digital Rights Management (DRM) and digital watermarking are commonly used for tracking and asserting ownership, blockchain adds an extra layer of verification.
Platforms like ScoreDetect streamline this process. For instance, its integration with Zapier connects to over 6,000 web apps, automating workflows to timestamp content as it’s created or updated. WordPress users can benefit from a dedicated plugin that captures every published or updated article, creating verifiable blockchain records while boosting SEO through Google’s E-E-A-T (Experience, Expertise, Authoritativeness, Trustworthiness) framework.
This blockchain-based approach is particularly valuable in industries like media, entertainment, legal services, and research. In these fields, proving the date and ownership of intellectual property can be crucial in resolving disputes. Unlike traditional copyright systems, which vary by country, blockchain timestamps offer a consistent, globally accessible method for establishing ownership across jurisdictions.
sbb-itb-738ac1e
Reducing Risks in Cross-Border Digital Operations
Expanding operations across borders comes with its fair share of challenges, particularly when it comes to regulatory compliance and protecting intellectual property. Businesses face threats like digital piracy, unauthorized content sharing, and navigating complex legal landscapes. For instance, penalties under the EU’s Digital Services Act and the UK’s Online Safety Act can climb into the billions. To mitigate these risks, companies need a combination of advanced technology and well-thought-out strategies tailored for international operations.
Preventing Digital Piracy and Unauthorized Use
Digital piracy is a major issue for industries like media, entertainment, and software. With massive volumes of global content, piracy has become a constant threat. Traditional enforcement methods often fall short as unauthorized material spreads quickly across borders.
One effective solution is invisible watermarking. Unlike visible marks that can be edited out, invisible watermarks embed unique identifiers into digital assets like images, videos, and audio files without altering their quality. These watermarks help businesses trace leaks and prove unauthorized distribution while ensuring legitimate users remain unaffected. This approach complements other tools like AI and blockchain for safeguarding digital assets.
Another layer of protection comes from automated monitoring systems. These tools continuously scan platforms worldwide for pirated content. For example, ScoreDetect’s AI-powered discovery tools achieve a 95% success rate in identifying infringing material, even bypassing common prevention measures. This allows businesses to catch and address piracy before it causes significant financial harm.
Automating Takedown Processes for Infringing Content
Detecting unauthorized content is just the first step – removing it quickly is equally important. Manual takedown processes often can’t keep up with the speed at which content spreads online, leaving companies vulnerable to revenue losses and reputational damage. Adding to the complexity, different regions have varying legal frameworks for handling takedowns. For example, the U.S. follows the notice-and-takedown model under the Digital Millennium Copyright Act (DMCA), while the EU Copyright Directive requires platforms to act proactively to prevent unauthorized content from being uploaded in the first place [6].
Automation offers a faster, more scalable solution. Tools like ScoreDetect’s automated takedown system boast a 96% success rate in removing infringing content from platforms, marketplaces, and social media. This speed is crucial, especially in jurisdictions with strict timelines. For instance, the UK’s Crime and Policing Bill mandates that platforms address takedown requests within 48 hours, with penalties of up to £10,000 for non-compliance by content managers [1].
Advanced systems employ multi-modal AI scanning to tackle infringement across various media types. These technologies combine natural language processing for text, computer vision for images and videos, and audio fingerprinting for sound. Benchmarks show that effective systems can act on infringing images in under a minute and videos in under two minutes [7].
Ensuring Accessibility and Compliance with Local Laws
Preventing piracy is just one piece of the puzzle. Businesses also need to comply with local laws around accessibility, anti-discrimination, and geo-blocking. The challenge lies in managing overlapping and sometimes conflicting regulations across different regions, which requires adapting content policies to meet local standards.
Geo-blocking is a practical tool for ensuring compliance. By restricting access to content based on geographic location, businesses can adhere to local licensing agreements and avoid potential diplomatic issues. Digital rights management (DRM) systems add another layer of control by setting expiration dates on media or limiting access to specific devices and IP addresses [2].
Localized translations and geo-blocking are especially important for businesses using a hub-and-spoke model, where a central team sets global policies and regional teams handle local execution. This ensures consistency while meeting region-specific requirements [3].
To stay ahead of potential legal conflicts, businesses can use strategic risk mapping. This involves conducting comparative legal analyses and running tabletop exercises to simulate regulatory actions in high-risk areas. These proactive measures prepare companies to respond effectively if and when authorities step in [1].
Building a Long-Term Cross-Border Compliance Program
Relying solely on reactive compliance strategies just doesn’t cut it anymore. To keep up with the complexities of cross-border operations, businesses need a well-structured, long-term compliance program. While short-term fixes can help reduce immediate risks, they don’t provide the sustained oversight necessary for global operations. Between 2022 and 2025, 85% of business executives reported that compliance requirements have grown increasingly complex [3]. To navigate this maze of regulations, companies must invest in automated systems capable of resolving conflicting rules across jurisdictions.
Vendor Management and Screening
Third-party vendors often pose significant compliance risks. To address this, it’s critical to include strict compliance clauses in vendor contracts and carry out thorough due diligence. This means verifying their security certifications, data handling protocols, and incident response plans [8]. Whether it’s a data processor, hosting provider, or content delivery network, every vendor must meet the same regulatory standards your business is held to – especially under regulations like GDPR.
For businesses dealing with digital content, this responsibility extends to the platforms where your content is shared. If a marketplace or social media site fails to meet takedown requirements or protect your watermarked assets, it can lead to liabilities that are tough to manage.
Training and Real-Time Monitoring
Generic, once-a-year training sessions won’t cut it. Employees need role-specific training that explains not just what the regulations are, but why they exist. For instance, content managers require different guidance than data processors or customer service teams [8]. When employees understand that GDPR is about protecting individual rights – not just creating more paperwork – they’re better equipped to make sound decisions in tricky situations [3].
Real-time monitoring is another critical piece of the puzzle. Companies using connected risk platforms report 83% greater efficiency in control mapping and 63% faster data reporting [8]. These platforms consolidate data from transaction records, access logs, and content management systems. When there’s a change in access controls, the system updates privacy assessments automatically, helping to prevent unauthorized IT practices. Such proactive measures not only strengthen compliance but also set the stage for smoother audits and continuous refinement.
Continuous Auditing and Improvement
Annual reviews are no longer enough to keep up with evolving compliance demands. Continuous monitoring ensures your business is always audit-ready [8]. Implement tracking systems that can flag potential issues before they escalate into full-blown violations. After completing major reporting cycles, conduct post-cycle reviews to pinpoint and address any delays or inefficiencies [3].
Tabletop exercises are another valuable tool. Simulate regulator requests or surprise audits in high-risk jurisdictions to uncover weaknesses in your documentation, response protocols, or team coordination [1]. For digital content businesses, these exercises might include demonstrating compliance with Article 30 of GDPR, testing the effectiveness of watermarks, or proving takedown response times. Automated workflows can make a huge difference, improving audit readiness by 50% [8].
Conclusion
Compliance risks are no small matter. Under the EU’s Digital Services Act, penalties can climb as high as 6% of global revenue, while the UK’s Online Safety Act imposes fines of up to £18 million or 10% of global turnover [1]. Even companies with the best intentions can find themselves in hot water without solid processes in place.
The businesses that succeed in this challenging landscape are those that make compliance a core part of their operations from the outset. This involves centralizing the mapping of regulatory requirements, adopting risk-based strategies, and using automation to manage the more complex aspects of compliance. Without these safeguards, expanding into new markets becomes a gamble [3].
Technology plays a key role in addressing these challenges. Tools like Digital Rights Management (DRM) systems help control access and prevent unauthorized copying, while AI-powered monitoring solutions can identify risky behaviors in real time. For companies managing digital content, platforms such as ScoreDetect offer advanced anti-piracy tools, quick content removal capabilities, and blockchain-backed proof of ownership – providing security without the need to store the actual digital files.
Prioritizing compliance fosters trust among customers, partners, and regulators. Companies that weave transparency, user empowerment, and jurisdiction-specific legal requirements into their operations are better equipped to handle regulatory hurdles [1]. This not only protects market access but also enhances reputation and creates a strong foundation for future growth.
The bottom line? Think of compliance as a strategic advantage. Invest in the right technologies, educate your teams on the reasons behind the rules, and stay proactive about regulatory updates. When compliance becomes second nature, it transforms from a barrier into a cornerstone of long-term success.
FAQs
What are the main differences between GDPR and CCPA/CPRA when it comes to data protection?
The GDPR (General Data Protection Regulation) and CCPA/CPRA (California Consumer Privacy Act/California Privacy Rights Act) share a common goal: safeguarding personal data. However, they differ significantly in their approach, scope, and enforcement.
The GDPR applies to companies operating within or targeting the European Union. It enforces strict rules like obtaining clear consent, limiting data collection to what’s necessary, and allowing individuals to request the deletion of their data (commonly known as the "right to be forgotten"). It covers all types of personal data and imposes hefty penalties for violations, making compliance a serious priority for businesses.
In contrast, the CCPA/CPRA is tailored to protect California residents. It grants specific rights, such as the ability to opt out of data sales, access the data companies have collected about them, and request corrections to inaccurate information. This regulation applies to businesses that meet certain criteria, including revenue thresholds or the volume of personal data they handle.
While both aim to improve privacy protections, the GDPR casts a wider net with stricter enforcement measures, whereas the CCPA/CPRA leans heavily on transparency and giving consumers more control over their data, particularly in the context of the U.S. market.
How do AI and blockchain technologies improve cross-border digital compliance?
AI simplifies the challenges of cross-border digital compliance by automating the tracking of intricate, multilingual regulations and spotting potential risks in real-time. It can sift through massive amounts of legal and transactional data from various jurisdictions, flagging irregularities and anticipating compliance issues before they arise. This not only cuts down on manual work but also lowers costs and reduces the likelihood of human error.
Blockchain brings an added layer of reliability by offering a tamper-proof, decentralized ledger for compliance-related activities. Whether it’s recording transactions, audit trails, or policy changes, blockchain ensures these records are easily verifiable, promoting transparency and trust. It also eliminates redundant paperwork, making regulatory audits far simpler.
ScoreDetect merges these two technologies to optimize compliance workflows. Its AI-powered tools identify unauthorized use of digital assets, while blockchain provides cryptographic proof of ownership. Together, they deliver secure, verifiable compliance, strengthening digital operations across borders.
How can businesses effectively manage cross-border data transfers?
To handle cross-border data transfers effectively, businesses need to focus on three main aspects: legal compliance, technical protections, and continuous oversight.
Start by mapping out where your data flows and ensuring you meet the regulations of each country involved. Legal tools like Standard Contractual Clauses (SCCs) or Binding Corporate Rules (BCRs) can help create a consistent legal framework for transferring data internationally.
Next, prioritize strong technical safeguards. This includes using end-to-end encryption, tokenization, and conducting regular cybersecurity audits. These measures are critical for protecting your data and ensuring its security throughout the transfer process.
Finally, adopt a proactive approach by keeping an eye on regulatory updates, performing regular privacy impact assessments, and maintaining detailed audit logs. This ongoing oversight helps you stay compliant with changing rules, reducing the risk of breaches and penalties while ensuring the secure management of global data transfers.

