Invisible watermarking embeds hidden data into media files like images, videos, or audio without affecting their appearance or quality. It’s a discreet way to protect content, trace its distribution, and verify authenticity. Unlike visible watermarks, these markers are undetectable to the human eye but can survive compression, resizing, and other edits, making them ideal for copyright protection and tamper detection.
Key Points:
- Purpose: Protects ownership, tracks usage, and ensures integrity of digital media.
- Techniques:
- Spatial Domain: Alters pixel values but is less resistant to compression.
- Frequency Domain: Embeds data in media’s frequency components, making it more durable.
- Applications: Used in photography, video streaming, AI-generated content, and document security.
- Advanced Tools: Modern systems like InvisMark and SynthID use AI and blockchain for stronger, tamper-proof watermarks.
Invisible watermarking is a reliable solution for safeguarding digital assets in an era of easy duplication and distribution.
How to Hide a Watermark in an Image
Understanding these embedding techniques is crucial, especially when considering how these marks resist removal attacks from bad actors.
sbb-itb-738ac1e
How Invisible Watermarking Works
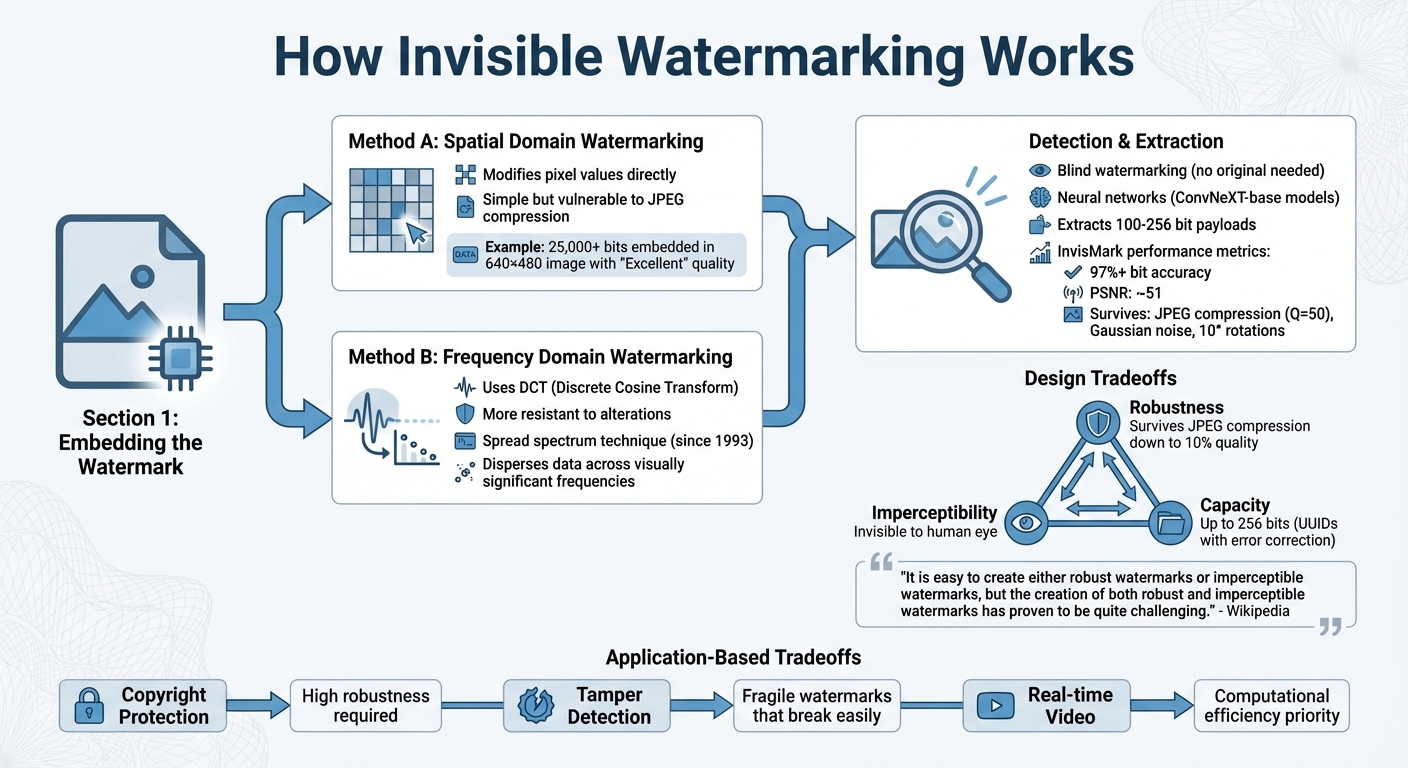
How Invisible Watermarking Works: Embedding to Detection Process
Embedding the Watermark
The process of embedding an invisible watermark begins with identifying areas within a media file where information can be hidden without affecting its appearance. These areas are chosen based on human perception, targeting spots where changes are least likely to be noticed. The goal is to keep the watermark undetectable to the human eye while ensuring it can be recognized by specialized software.
Two primary methods are used for embedding watermarks. Spatial domain watermarking modifies less significant pixels or samples directly. While this approach is straightforward, it’s vulnerable to strong JPEG compression, which can erase the watermark. On the other hand, frequency domain watermarking transforms the content using techniques like the Discrete Cosine Transform (DCT). This method is more resistant to alterations and manipulation [3].
A notable technique involves quantization manipulation in JPEG images. By tweaking values near rounding thresholds – like those close to 0.5 – during the quantization step, data can be embedded without significantly affecting the image’s quality. For example, researchers managed to embed over 25,000 bits of information into a 640×480 image while maintaining "Excellent" visual quality [3].
Another approach, spread spectrum techniques, disperses watermark data across the image’s most visually significant frequencies. This makes the watermark highly resistant to attacks like cropping or rotation, though it can be computationally intensive [1][3]. The first successful application of this method dates back to 1993 [1].
Once the watermark is embedded, the challenge becomes extracting it reliably, even after the media undergoes alterations.
Detecting and Extracting Watermarks
After embedding, the next step is to detect and retrieve the watermark, even when the media has been compressed, resized, or otherwise altered. These distortions can make detection tricky, so advanced algorithms often use affine correction to align the content with the original embedding grid [3].
Modern detection systems use a variety of techniques. Blind watermarking schemes are particularly useful because they don’t require access to the original, unwatermarked content [2]. Cutting-edge systems leverage neural networks, such as ConvNeXT-base models with sigmoid layers, to extract payloads of 100 or 256 bits from watermarked images [4]. To ensure accuracy, these systems may incorporate bit-wise majority logic or error-correction codes. For instance, in November 2024, Microsoft’s Responsible AI team introduced InvisMark, a system that maintained over 97% bit accuracy across various manipulations – including JPEG compression (with a quality factor of 50), Gaussian noise, and 10° rotations. InvisMark also achieved a peak signal-to-noise ratio (PSNR) of about 51 [4]. Embedding UUIDs with error-correction codes can further enhance decoding reliability [4].
Design Tradeoffs
Balancing the strength of the watermark with its invisibility is a critical design challenge. Systems must carefully weigh robustness, imperceptibility, and capacity [1].
"In general, it is easy to create either robust watermarks or imperceptible watermarks, but the creation of both robust and imperceptible watermarks has proven to be quite challenging."
– Wikipedia [1]
Strengthening a watermark to improve its robustness often makes it more visible, which can degrade the quality of the media [1][3]. Similarly, embedding larger amounts of data (higher capacity) can weaken robustness, as the signal becomes more prone to interference [1].
The tradeoffs depend on the intended application. For example, copyright protection demands high robustness to withstand attacks like cropping or compression. Some robust watermarking methods can survive JPEG compression with quality factors as low as 10%, though they may fail at 5% [3]. On the other hand, tamper detection in sensitive documents relies on "fragile" watermarks that vanish after even minor modifications, signaling content changes [1]. Meanwhile, real-time uses, such as Video on Demand, require computational efficiency, which can limit the complexity of the algorithms used [3].
Technical Methods for Invisible Watermarking
Spatial Domain Watermarking
Spatial domain watermarking works by directly modifying the pixel values of an image. A common technique here is LSB modification, where the watermark is embedded into the least significant bits of the pixel data [4]. This method is simple and quick, making it ideal for straightforward applications. However, it has a major drawback: it’s highly fragile. Even basic operations like JPEG compression can erase the watermark entirely since these operations typically discard the least significant bits during the quantization process [3]. Because of this vulnerability, LSB methods are more effective for detecting tampering rather than providing robust copyright protection. For stronger resilience, frequency domain techniques are often preferred.
Frequency Domain Watermarking
Frequency domain watermarking takes a different approach by embedding the watermark into the frequency components of an image. Techniques like DCT (Discrete Cosine Transform) and DWT (Discrete Wavelet Transform) are commonly used to convert the image into frequency coefficients before embedding the watermark [4]. This method offers greater resistance to compression and other routine image processing tasks. For instance, studies have shown that DCT-based watermarks remain detectable even when JPEG quality drops as low as 10% [3].
This approach is widely used in industrial applications, including the commercial implementation of Stable Diffusion. Some systems go a step further by incorporating Human Visual System (HVS) models, which identify areas in the image where changes are less noticeable. This ensures that the watermark remains invisible to the human eye while maintaining its robustness [2]. Additionally, cutting-edge approaches now integrate machine learning and blockchain technologies to further enhance the reliability and security of watermarking systems.
Machine Learning and Blockchain Integration
Modern watermarking techniques are increasingly leveraging neural network architectures like HiDDen, StegaStamp, and InvisMark. These systems use encoder-decoder models to embed hidden messages as "residuals" within the image [4]. Neural network-based methods can embed payloads of up to 256 bits with an impressive accuracy rate of over 97%, even after the image undergoes manipulations [4].
blockchain technology adds an extra layer of security by serving as a decentralized ledger for content provenance. While the watermark acts as an embedded identifier, the blockchain stores metadata such as ownership records and timestamps. Importantly, the actual digital asset isn’t stored on the blockchain, but the metadata creates a verifiable chain of custody. This ensures that even if the original metadata is stripped away, the watermark can still serve as a trusted record of the content’s origin [4].
"Image watermarking offers an alternative solution by inserting an imperceptible identifier within the content itself. This allows for exact matching and retrieval of associated provenance from databases."
– Microsoft Responsible AI [4]
To make these systems more robust, training often includes "noiser" modules that simulate harsh conditions like 25% random cropping or 10° rotations. These modules help ensure that the watermark can survive even under extreme scenarios [4]. The adoption of advanced neural architectures, such as ConvNeXT, reflects the industry’s push toward creating watermarks that are not only invisible but also nearly indestructible.
Applications of Invisible Watermarking
Images, Videos, and Audio
Invisible watermarking adjusts its approach based on the type of media. For images, watermarks are embedded within JPEG DCT coefficients, allowing them to survive even when image quality is reduced to as low as 10% during compression [3]. Advanced techniques now use quantization errors to embed data without increasing file size [3].
When it comes to video watermarking, advancements have aligned with MPEG-4 standards. Techniques like Shape Adaptive-Discrete Wavelet Transform (SA-DWT) embed watermarks into specific video objects [2]. This ensures that even if an object is extracted from a scene, the watermark stays intact. Unlike earlier methods, these systems don’t require the original unwatermarked content for detection, making them highly practical for applications such as Video On Demand services [2][3].
In October 2025, Google scaled up its SynthID-Image system, watermarking over 10 billion images and video frames across its platforms. This system, developed by Sven Gowal and a team of 25 researchers, uses deep learning to embed invisible watermarks that remain detectable even after manipulations like cropping, resizing, and color adjustments [5]. As the team explained:
"SynthID-Image has been used to watermark over ten billion images and video frames across Google’s services and its corresponding verification service is available to trusted testers."
– Sven Gowal et al., Researchers [5]
These advancements are paving the way for watermarking in documents and AI-generated content.
Documents and AI-Generated Content
Watermarking has also expanded into text-based and AI-generated content. Modern methods can embed payloads of up to 256 bits, enabling Universally Unique Identifiers (UUIDs) with error correction [4]. This provides a form of "soft binding" for content provenance. Even if metadata is stripped away by social media platforms or malicious actors, the watermark remains embedded within the content [4].
For AI-generated imagery from platforms like DALL-E 3 or Stable Diffusion, watermarking is now integrated into the generation process. Techniques like InvisMark use neural watermarking to achieve a Peak Signal-to-Noise Ratio (PSNR) of around 51 and a Structural Similarity Index Measure (SSIM) of 0.998. These watermarks are nearly invisible while maintaining more than 97% bit accuracy, even after manipulations [4]. This is a crucial step in addressing the challenges of hyper-realistic deepfakes and combating misinformation.
As Microsoft’s Responsible AI team notes:
"Image watermarking offers an alternative solution by inserting an imperceptible identifier within the content itself. This allows for exact matching and retrieval of associated provenance from databases."
– Microsoft Responsible AI [4]
Embedding secure identifiers in content is becoming essential across industries.
Industry Applications
The versatility of these watermarking techniques has led to their adoption across various industries. In media and entertainment, watermarking is used for traitor tracing (also known as fingerprinting), where each distributed copy receives a unique watermark to trace the source of leaks [2][3]. This is especially valuable for streaming services and early-release content, where unauthorized sharing poses financial risks.
Legal firms and government agencies rely on "fragile" or "semi-fragile" watermarks that break if documents are tampered with, providing proof of integrity [4]. At the same time, digital businesses and e-commerce platforms use watermarking to protect product images, preventing competitors from misusing visual assets. The technology also supports broadcast and distribution networks by securing wireless video communications and internet-based content delivery [2].
As researchers Nikolay Mateev and Lidong Zhou from Cornell University have observed:
"As digital images and video become more popular, there is a pressing need for a scheme to protect ownership… That label must uniquely identify the copyright owner, and should also allow distribution of the particular copy to be tracked."
– Nikolay Mateev and Lidong Zhou, Cornell University [3]
The move toward large-scale AI watermarking reflects a growing trend. These systems now protect billions of assets across global platforms, balancing robust tracking capabilities with minimal impact on visual quality [5].
How ScoreDetect Implements Invisible Watermarking
ScoreDetect’s Watermarking Technology
ScoreDetect has developed a way to protect content without compromising its quality. By embedding invisible, non-intrusive watermarks directly into images, videos, audio files, and documents, the platform ensures your content looks and sounds exactly as intended. These hidden identifiers remain intact even after cropping, resizing, compression, or re-encoding [6][8].
What sets ScoreDetect apart is its ability to verify ownership instantly, even if the file has undergone multiple modifications. This makes it a powerful tool for safeguarding your digital assets [9].
Complete Content Protection Workflow
ScoreDetect’s Enterprise plan offers a comprehensive four-step system to protect your content: Prevent, Discover, Analyze, and Take Down.
- Prevent: Invisible watermarks are embedded into your digital assets before they are distributed.
- Discover: Using advanced web scraping technology, ScoreDetect monitors where your content appears online, avoiding most prevention measures with a 95% success rate.
- Analyze: The system compares discovered content to your original watermarked files, providing concrete evidence of unauthorized use.
- Take Down: Automated delisting notices are sent out, achieving a take-down success rate of over 96%.
This workflow is designed to integrate smoothly with ScoreDetect’s broader security tools. It also connects with over 6,000 web applications through Zapier, enabling you to create workflows tailored to your unique needs.
Blockchain Timestamping for Proof of Ownership
To further enhance content protection, ScoreDetect leverages blockchain technology to create tamper-proof ownership certificates. Instead of storing the entire asset, the system saves metadata – like your name, asset description, and creation time – alongside a cryptographic hash (using SHA-256) of your content [7]. As explained by Mentaport:
"An immutable certificate is a blockchain-stored digital record proving the ownership, authenticity, and history of your content. Unlike traditional digital certificates, it cannot be altered or deleted, ensuring the highest level of security and transparency."
– Mentaport [6]
Every modification to your content generates a new blockchain record, creating an unbroken chain of custody [7]. If any tampering occurs, the hash mismatch instantly exposes the changes [7]. For WordPress users, the plugin automatically logs every article published or updated, providing verifiable proof of ownership while boosting SEO through Google’s E-E-A-T (Experience, Expertise, Authoritativeness, and Trustworthiness) framework.
Conclusion
Key Takeaways
Invisible watermarking has become essential in a world where digital content can be copied and altered with ease. Unlike metadata, which can be erased during editing, these embedded markers stay intact through processes like compression, resizing, cropping, and even re-encoding. Techniques such as Discrete Cosine Transform (DCT) and Discrete Wavelet Transform (DWT) ensure watermarks remain detectable, even when image quality drops to just 10% after JPEG compression [3].
What makes this technology so effective is its ability to remain invisible to the human eye while offering powerful forensic tools. These watermarks can trace unauthorized content back to its source, which is why industries like healthcare, media, and entertainment use them to safeguard their valuable assets.
Taking these principles further, platforms like ScoreDetect combine invisible watermarking with blockchain timestamping and automated monitoring to offer a comprehensive solution. Its four-step process – Prevent, Discover, Analyze, and Take Down – covers every aspect of content protection. From embedding watermarks before distribution to achieving a 96% success rate in removing unauthorized copies, this system provides a reliable way for organizations to manage and protect digital assets across various platforms. It’s a blend of strong technical capabilities and operational efficiency that helps enforce copyright effectively.
FAQs
How does invisible watermarking protect content while staying undetectable?
Invisible watermarking embeds a subtle, undetectable signal into digital files like images, videos, or documents. By using advanced algorithms, it hides this watermark in areas that the human eye or ear won’t notice. For instance, it might tweak frequency components or adjust the least-significant bits of pixel values in a way that leaves the content’s appearance and quality intact. This approach ensures the watermark stays hidden while maintaining quality metrics like PSNR (Peak Signal-to-Noise Ratio) and SSIM (Structural Similarity Index).
To strengthen protection, invisible watermarking uses methods like redundancy, error correction, and spread-spectrum encoding, which scatter the watermark across various parts of the content. This makes it resistant to alterations such as compression, resizing, cropping, or changes in brightness. Advanced tools can even tailor the watermark to the unique features of the content, ensuring it remains durable without being visible. When paired with blockchain technology, it provides verifiable proof of ownership and helps protect the content from unauthorized use.
What’s the difference between spatial-domain and frequency-domain watermarking?
Spatial-domain watermarking works by embedding a watermark directly into the media file by adjusting pixel or sample values. For example, it might modify the least-significant bits of an image or adjust audio amplitudes. This approach is straightforward, quick, and supports larger data capacities. However, the downside is that these watermarks are fragile – they can be easily removed or degraded by processes like compression, cropping, or resizing.
Frequency-domain watermarking takes a different route. It converts the content into a spectral representation using techniques like DCT (Discrete Cosine Transform), DWT (Discrete Wavelet Transform), or FFT (Fast Fourier Transform). The watermark is then embedded into specific transform coefficients, making it more resilient to compression, noise, and geometric alterations. This method also ensures the watermark remains nearly invisible. While it requires more computational power and supports smaller data payloads, it provides greater durability and subtlety.
ScoreDetect combines both approaches to strike the right balance between robustness, speed, and data capacity. The method is tailored to suit the specific requirements of images, videos, or documents, ensuring optimal performance for each type of media.
How does blockchain improve the security of invisible watermarking?
Blockchain strengthens the security of invisible watermarking by storing a cryptographic checksum of the watermarked content on an unchangeable ledger. This makes it virtually impossible to tamper with the watermark while also providing undeniable proof of ownership.
With blockchain, you can ensure that the hidden watermark stays intact and unchanged, delivering a dependable solution for safeguarding and verifying your digital assets.

