Protecting your digital content from theft and false ownership claims is easier with invisible watermarking. This method embeds hidden identification markers directly into your files, ensuring you can prove ownership even if your content is copied, edited, or shared. Unlike visible watermarks, invisible ones don’t affect the appearance or quality of your work, making them ideal for images, videos, and sensitive documents. This is particularly effective for protecting e-books and other digital publications. Here’s how you can safeguard your creations:
- Use advanced watermarking tools like ScoreDetect to embed hidden ownership details.
- Add unique watermarks to each copy to trace leaks or misuse.
- Leverage blockchain technology for a permanent, tamper-proof record of ownership.
Invisible watermarks help protect your rights, prevent financial loss, and simplify dispute resolution. These tools ensure your digital assets remain secure while maintaining their integrity and usability.
Photoshop – How to make a watermark…..invisible!
What Is Invisible Watermarking and Why Use It
Invisible watermarking is a method of protecting digital files by embedding information directly into the file’s data in a way that’s undetectable to the human eye. Unlike visible watermarks, which use logos or text overlays, this technique alters specific pixels or data points in images or videos without affecting their appearance. The embedded information serves as a digital certificate of authenticity (often paired with ownership timestamps), ensuring that ownership details stay with the file wherever it goes [2]. This makes it a powerful tool for safeguarding intellectual property throughout the content’s lifecycle.
The European Union Intellectual Property Office (EUIPO) explains it well:
A digital watermark is a piece of information that is permanently embedded in a digital file, certifying its authenticity and source [2].
Unlike visible watermarks, which can distract from content and are often easy to remove, invisible watermarks remain hidden within the file’s structure. They can only be accessed using specialized software or tools, making them a more secure option [2].
How Invisible Watermarking Works
The process involves embedding unique identifiers directly into the file’s data. In images, this could mean tweaking pixel values in ways that don’t affect visual quality. For videos, these subtle changes are made across multiple frames. Despite these modifications, the content remains visually untouched [2][3].
Invisible watermarks can encode various types of information, including:
- Content-ID marks: Identifying the specific content.
- Owner-ID marks: Embedding ownership details.
- User-ID marks: Tracking individual recipients.
- Network-ID marks: Mapping distribution paths [2].
One of the standout features of invisible watermarking is its durability. These watermarks are designed to withstand common file alterations like compression, resizing, cropping, color adjustments, and even format conversions. This ensures that proof of ownership remains intact, no matter how the file is edited or shared [2][3]. The UKOLN research organization highlights this practicality:
By embedding Intellectual Property data… the digitiser can demonstrate they are the creator and disseminate this information with every copy, even when the digital object has been uploaded to a third-party site [3].
Invisible watermarks come in two types: private and public. Private watermarks offer higher security by requiring the original file or a decoding key to detect them. Public watermarks, on the other hand, can be identified by anyone with the appropriate software [2]. This flexibility ensures that ownership verification remains both secure and accessible.
Main Benefits of Invisible Watermarking
One of the biggest advantages is providing irrefutable proof of ownership. In cases of disputes, creators can use specialized tools to uncover the embedded watermark, establishing ownership of digital media without relying on metadata or external records that could be altered [2][3].
Another key benefit is that invisible watermarks preserve the visual quality of the content. Unlike visible watermarks, which can disrupt the viewer’s experience, invisible marks are non-invasive, making them ideal for professional photography, fine art, and other visually sensitive works [3].
Invisible watermarking also offers tracking capabilities. By embedding unique watermarks in different copies, creators can pinpoint the source of unauthorized leaks. This feature is especially valuable for high-stakes content like pre-release media, confidential documents, or proprietary designs [2].
| Feature | Visible Watermarking | Invisible Watermarking |
|---|---|---|
| Appearance | Overt logos, text, or stamps | Hidden in file data, imperceptible |
| Core Function | Deterrence and branding | Authentication, tracking, proof of ownership |
| Robustness | Low; easy to crop or remove | High; survives file alterations |
| Impact on Content | Can be distracting | Non-invasive; no effect on viewing experience |
Invisible watermarks also support tamper detection. Fragile watermarks are designed to break if the file is altered, alerting owners to unauthorized changes. Meanwhile, robust watermarks can endure modifications, ensuring that proof of ownership remains intact regardless of edits [2][3].
This technology is versatile and can be applied across many industries. Whether it’s protecting academic research, financial documents, manufacturing blueprints, or creative works, invisible watermarking offers a reliable way to assert and maintain ownership without compromising usability or appearance.
How to Prevent Ownership Disputes with Watermarking
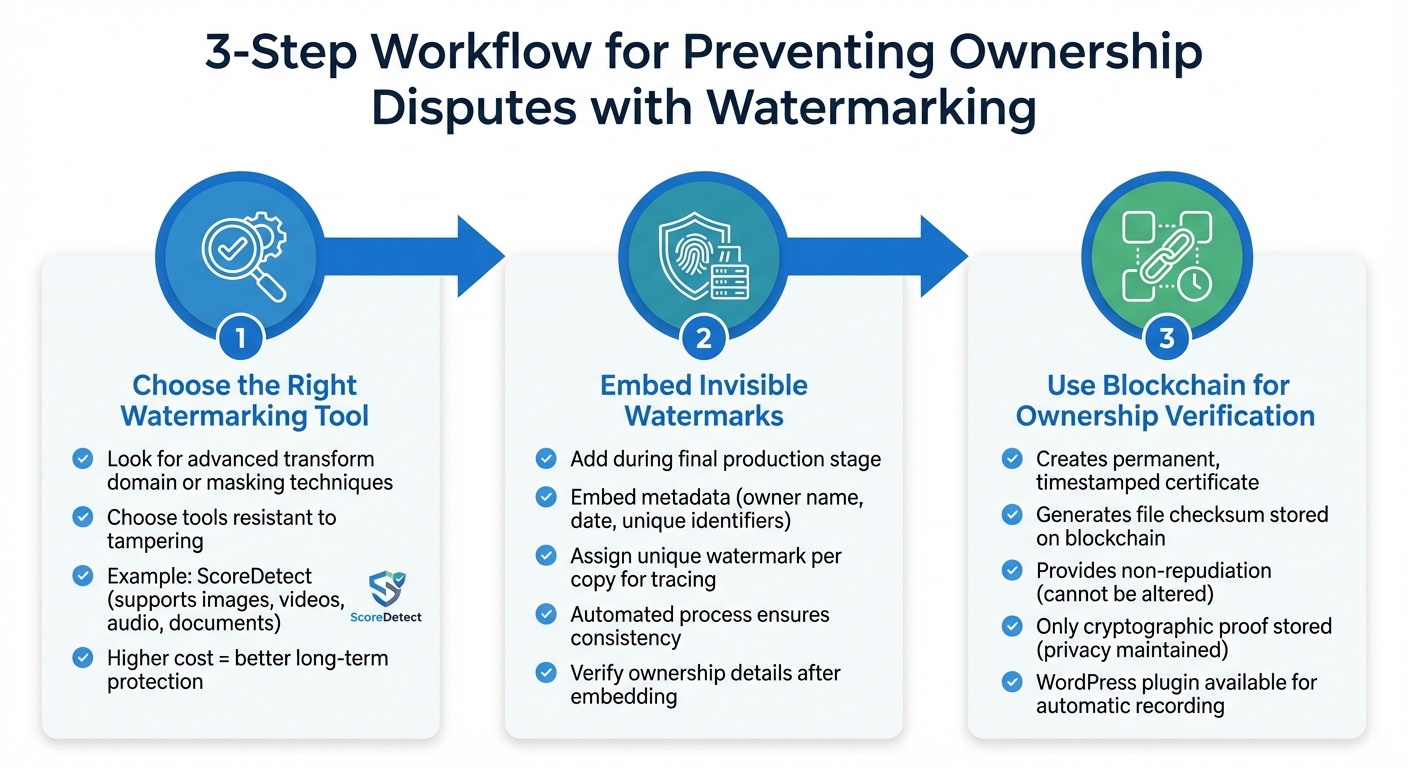
3-Step Process to Prevent Ownership Disputes with Watermarking
Securing undeniable proof of ownership for your digital content doesn’t have to be complicated. Here’s a straightforward, three-step approach to help you protect your assets and avoid ownership disputes.
Step 1: Choose the Right Watermarking Tool
The first step in safeguarding your content is selecting a watermarking tool that matches your needs. Look for tools equipped with advanced transform domain or masking techniques, as these methods are far more resistant to tampering or accidental loss during file processing compared to basic bit-wise alterations.
For instance, ScoreDetect is a versatile option that works with images, videos, audio files, and documents. It’s designed to integrate seamlessly into various industries, from academic research and financial reports to creative projects and proprietary designs. While more robust watermarking solutions may come with a higher price tag, they can save you significant costs and headaches by preventing disputes over ownership down the road [2].
Step 2: Embed Invisible Watermarks
Invisible watermarks are your secret weapon against unauthorized use. These should be added during the final production stage to ensure they remain intact through any edits or modifications.
Embedding metadata – such as the owner’s name, date, and unique identifiers – helps distinguish each transaction. You can even assign a unique watermark to every copy of your content, making it possible to trace unauthorized sharing back to a specific user or event.
With ScoreDetect, this process is automated, ensuring watermarks remain intact even after substantial alterations to the file. Its advanced technology strikes a balance between durability and maintaining the original quality of your content. Plus, automation minimizes human error and ensures consistency across all your files. After embedding, verify the ownership details to complete the protection process.
Step 3: Use Blockchain for Ownership Verification
For the ultimate proof of ownership, record your content on the blockchain. This step creates a permanent, timestamped certificate that establishes when your work was created or published. ScoreDetect simplifies this by generating a checksum of your file and storing it on the blockchain, offering non-repudiation – a guarantee that the record cannot be altered or disputed [1].
Importantly, only cryptographic proof is stored on the blockchain, not the actual content, ensuring your privacy while providing legally sound evidence of ownership. These certificates include key details like the registration date, copyright owner’s name, work title, a SHA256 hash of the file, and public blockchain URLs for anyone to verify the certificate’s authenticity.
For WordPress users, ScoreDetect even offers a plugin that automatically records every article you publish or update, eliminating the need for manual intervention. When combined with invisible watermarking, this blockchain record creates a solid, legally defensible chain of custody for your digital assets, ensuring your ownership is always protected.
sbb-itb-738ac1e
Adding Watermarking to Your Workflow
Once your watermarking system is set up, automating the process is a smart move – especially when dealing with large volumes of files. By embedding watermarks during the production stage, you ensure that every piece of content is safeguarded from the moment it’s created. This streamlined approach reduces the risk of manual errors and guarantees consistent protection across your digital assets [2].
Automate Watermarking with ScoreDetect
ScoreDetect takes watermarking to the next level by integrating seamlessly with Zapier, which connects to over 6,000 web applications. This means you can automatically watermark content as it flows through your production pipeline – whether it’s blog posts, videos, or digital documents. The system also handles encryption and digital signing, so you don’t have to [1].
For WordPress users, the Timestamps plugin offers an easy way to automatically apply watermarks and generate blockchain certificates every time you update an article. These tools simplify the process, ensuring your content is always protected without extra effort.
Once you’ve automated watermarking, the next step is to keep an eye on your content to ensure it’s not being misused.
Monitor and Enforce with Discovery Tools
Watermarking is just the first layer of protection. ScoreDetect’s Enterprise suite adds another by using intelligent web scraping to identify unauthorized copies of your content. With a 95% success rate, the system scans the web, matches found material against your protected files, and provides solid evidence of misuse. This acts as a digital notary for your intellectual property.
Beyond detection, ScoreDetect also automates enforcement. Its delisting feature boasts a 96% takedown rate, helping you efficiently remove pirated content. This complete workflow – from watermarking to monitoring and takedown – eliminates the need for manual oversight. And with industries like film losing between $40 billion and $97.1 billion annually to piracy [4], tools like these are critical for keeping your digital assets secure on a large scale.
Conclusion
Ownership disputes can stall projects, tarnish reputations, and lead to hefty legal fees. Invisible watermarking provides a practical way to safeguard your digital files by embedding authentication data directly into them – without affecting their quality or appearance. This means you can still prove ownership even if your content is cropped, compressed, or shared on third-party platforms [2][3].
Beyond ownership proof, watermarking helps track and discourage unauthorized use. Tools like ScoreDetect take it a step further by automating the watermarking process, monitoring for misuse, and managing takedown requests – all in one platform. When combined with blockchain verification and advanced discovery tools, these measures create a strong shield for your digital assets.
FAQs
What’s the difference between invisible and visible watermarking?
Invisible watermarking works by embedding identifying details directly into a digital file’s structure. This method doesn’t change the content’s appearance and remains undetectable to the human eye. It’s designed to withstand common edits like compression or resizing, and specialized tools are needed to detect it. This makes invisible watermarking a great option for safeguarding ownership without disrupting the user experience.
Visible watermarking, in contrast, involves placing noticeable elements – like logos or text – over the content. These marks clearly signal ownership and act as a deterrent to unauthorized use. However, they can often be removed and may reduce the visual appeal of the content.
Invisible watermarks provide a subtle yet durable way to prove ownership, while visible watermarks offer a more overt, though less secure, form of protection.
Can invisible watermarks be altered or removed?
Invisible watermarks are crafted to be challenging to spot, modify, or erase. Yet, no system is entirely impervious. Sophisticated techniques, including those powered by generative AI, can sometimes interfere with or eliminate these watermarks.
Although invisible watermarks offer strong protection for digital assets, relying on them alone isn’t enough. Pairing them with additional security measures is crucial to better safeguard content from unauthorized use or potential conflicts.
How does blockchain make watermarking more secure?
Blockchain technology strengthens the security of watermarking by linking a digital watermark’s unique checksum to an unchangeable ledger. This creates tamper-proof, verifiable ownership records, offering clear and reliable proof of ownership.
If someone tries to modify the content or its watermark, it can be identified immediately. This makes blockchain an effective solution for safeguarding digital assets and confidently addressing ownership disputes.

