AI-generated content is everywhere, and watermarking is one of the main tools we rely on to protect digital assets. But here’s the problem: advanced AI systems are now capable of removing or forging watermarks with alarming precision. For example, attacks like "SemanticRegen" and "UnMarker" can erase or manipulate watermarks without damaging image quality, leaving creators vulnerable to misuse and fraud.
Key Takeaways:
- Watermark Removal: AI uses techniques like diffusion-based regeneration and spectral manipulation to erase watermarks.
- Watermark Forgery: Attackers can embed fake watermarks using AI, leading to false claims of ownership.
- Traditional Watermarks Fail: Older methods can’t withstand modern AI attacks, with detection rates dropping as low as 6.3%.
- New Solutions: Emerging strategies include embedding watermarks in textured areas, blockchain timestamping for proof of ownership, and AI-powered monitoring for spotting misuse.
Why It Matters:
With millions of AI-generated images created daily, protecting intellectual property is more challenging than ever. Combining advanced watermarking techniques with blockchain verification and automated enforcement offers a stronger defense against these threats.
The battle between watermarking technologies and AI attacks is ongoing, but new tools are stepping up to safeguard digital assets in this evolving landscape.
AI watermarks can never work.
How AI Attacks Digital Watermarks
AI systems have developed two main strategies to compromise digital watermarks: removal and forgery. These methods create serious challenges for businesses striving to safeguard their digital assets, and they continue to evolve at a fast pace.
AI can bypass watermarks by reconstructing images or altering the mathematical patterns that underpin them. Let’s break down how these attack techniques work.
Watermark Removal Attacks
One common approach is diffusion-based regeneration. This method introduces noise to an image and then applies denoising techniques to reconstruct it, effectively erasing high-frequency watermarks while keeping the main content intact [1][3].
"The very generative power that enables complex edits can be leveraged to wash out embedded watermarks that were designed to resist conventional perturbations." – Yunyi Ni, Researcher, Xidian University [1]
Another method focuses on disrupting spectral amplitudes, where many robust watermarks are embedded. Known as the "UnMarker" attack, this technique disturbs patterns in the frequency domain, reducing the ability to detect semantic watermarks to just 43% [4].
In May 2025, researchers introduced SemanticRegen, a sophisticated three-stage attack. By combining vision-language models with diffusion-based inpainting, this method removes background watermarks while maintaining the integrity of the foreground. It achieves a 12% improvement over earlier techniques and works effectively across systems like TreeRing, StegaStamp, StableSig, and DWT/DCT [5].
Watermark Forgery Attacks
Watermark forgery allows attackers to embed fake watermarks into content they don’t own. Using tools like generative adversarial networks (GANs) and few-shot learning, attackers can replicate authentic watermarks and overlay them onto malicious content, including deepfakes or fake news. This can lead to false attributions, harm reputations, and implicate innocent individuals [8].
Frameworks such as "Warfare" take this a step further by enabling watermark removal or forgery at unprecedented speeds. Using GAN-based methods, these frameworks can process images up to 11,000 times faster than earlier diffusion-based techniques [8].
"Existing watermarking algorithms only withstand attacks when the adversary has no access to the detection algorithm." – Google Workshop on Generative AI [8]
When watermarks are removed or counterfeited, companies lose critical protections for their intellectual property. This opens the door to unauthorized commercial use, makes it harder to track leaks, and undermines systems of trust. If counterfeit watermarks can be created, verifying content authenticity becomes nearly impossible.
Why Traditional Watermarking Methods Fail
Traditional watermarking methods, designed to handle basic edits, fall short against modern AI techniques. These advanced systems can reconstruct images by learning patterns, effectively bypassing the protections that traditional watermarks offer. This gap highlights how AI takes advantage of these outdated defenses.
Vulnerability to Advanced AI Attacks
Diffusion models, for example, treat watermarks as mere noise. During image reconstruction, these models erase high-frequency watermark signatures with ease [1] [3].
"In the limit of a very strong diffusion attack, the best decoder does no better than random guessing." – Yunyi Ni et al., Researchers [1]
Recent tests show that even advanced watermarking systems struggle to detect altered images, with accuracy dropping significantly. The UnMarker attack, in particular, targets the spectral amplitudes where watermarks are embedded, systematically dismantling their effectiveness [4]. Another common issue arises with fixed, non-adaptive watermark patterns. These can be exploited through averaging attacks, where attackers combine multiple watermarked images to uncover and remove the underlying pattern [9].
Inconsistent Detection Standards
Beyond technical flaws, inconsistent standards across the watermarking industry create additional vulnerabilities. Some systems embed watermarks during image creation, while others apply them afterward. Certain methods focus on surviving physical distortions like printing and scanning, while others aim for resilience in the frequency domain. This lack of a unified approach leaves room for exploitation [1] [4].
"Current ‘robust’ watermarks sacrifice security for distortion resistance, providing insights for future watermark design." – Zhongjie Ba et al., Researchers [6]
The balance between watermark strength and visual quality further complicates matters. Stronger watermarks may resist attacks better but often introduce visible artifacts. On the other hand, subtle watermarks are less noticeable but easier to remove. Most traditional systems rely on an "Encoder-Noise-Decoder" framework, which struggles to strike the right balance. When attackers use channel-aware feature extraction, they can evade detection with a 60% improvement rate, all while preserving the image’s visual quality [6].
Solutions: Adaptive Watermarking Technologies
Modern watermarking systems have become smarter, adapting in real time to the unique characteristics of each image. By analyzing factors like visual complexity and edge entropy, these systems embed stronger watermarks in textured areas while using subtler marks in smoother regions. This approach maintains image quality while making it harder for AI to remove the watermarks.
Advanced techniques now rely on hybrid domain transformations, combining methods like DWT, HD, and SVD to create multi-layered defenses against geometric distortions and noise-based attacks. These systems achieve impressive metrics, such as an average PSNR of 45.34 dB and an SSIM of 0.9987 [12]. These hybrid transformations are a key step in making watermarks more resilient and harder to bypass.
Some cutting-edge frameworks also incorporate diffusion model priors during their training phase. By simulating potential manipulations attackers might use, these systems build resistance before they are even deployed. For example, the VINE system uses SDXL diffusion models and specific training augmentations to withstand image-to-image edits, which are known for erasing high-frequency watermark signals [1].
Blockchain-Enhanced Timestamping
One of the fundamental challenges with pixel-level watermarks is their vulnerability to AI regeneration attacks, which can add noise and reconstruct images to effectively remove the watermark [3]. Even when a watermark remains visible, tools like UnMarker can drastically reduce detection rates to just 43% [4]. Blockchain technology offers a solution by creating an immutable record that exists independently of the image file.
When content is registered using blockchain-enhanced systems, a cryptographic checksum captures the exact state of the digital asset at a specific moment. This timestamp is stored on a decentralized ledger, providing verifiable proof of ownership – even if the watermark is stripped from the file.
Platforms like ScoreDetect use blockchain timestamping to log content checksums without storing the actual digital files. These systems generate verifiable certificates that include SHA256 hashes, public blockchain URLs, and registration dates, all signed by ScoreDetect Limited. For creators and businesses managing large collections of digital assets, this creates an unalterable chain of custody. The platform integrates seamlessly with over 6,000 web apps via Zapier and offers a WordPress plugin that timestamps every new or updated article automatically. Beyond ownership verification, these tools also enable active monitoring to further protect digital assets.
AI-Powered Monitoring and Automated Takedowns
While blockchain verification secures ownership, AI-powered monitoring takes on the task of tracking unauthorized use across the web. Modern enterprise systems use intelligent web scraping, achieving a 95% success rate in bypassing prevention measures. These tools continuously scan websites, platforms, and marketplaces to identify unauthorized appearances of protected content.
Once unauthorized use is detected, automated enforcement tools match the content against registered assets using visual signatures, metadata, and blockchain timestamps. This eliminates the need for manual tracking and simplifies takedown processes.
ScoreDetect’s enterprise features streamline the entire enforcement process. After identifying unauthorized content, the system generates delisting notices, achieving a takedown success rate of over 96%. Additionally, cryptographic watermarking with zero-knowledge proofs currently takes about 5.4 minutes to generate proof [11]. With ongoing optimizations, this process is expected to be reduced to just seconds, making real-time verification a practical option for managing large volumes of content.
sbb-itb-738ac1e
Attack Methods vs. Adaptive Defenses
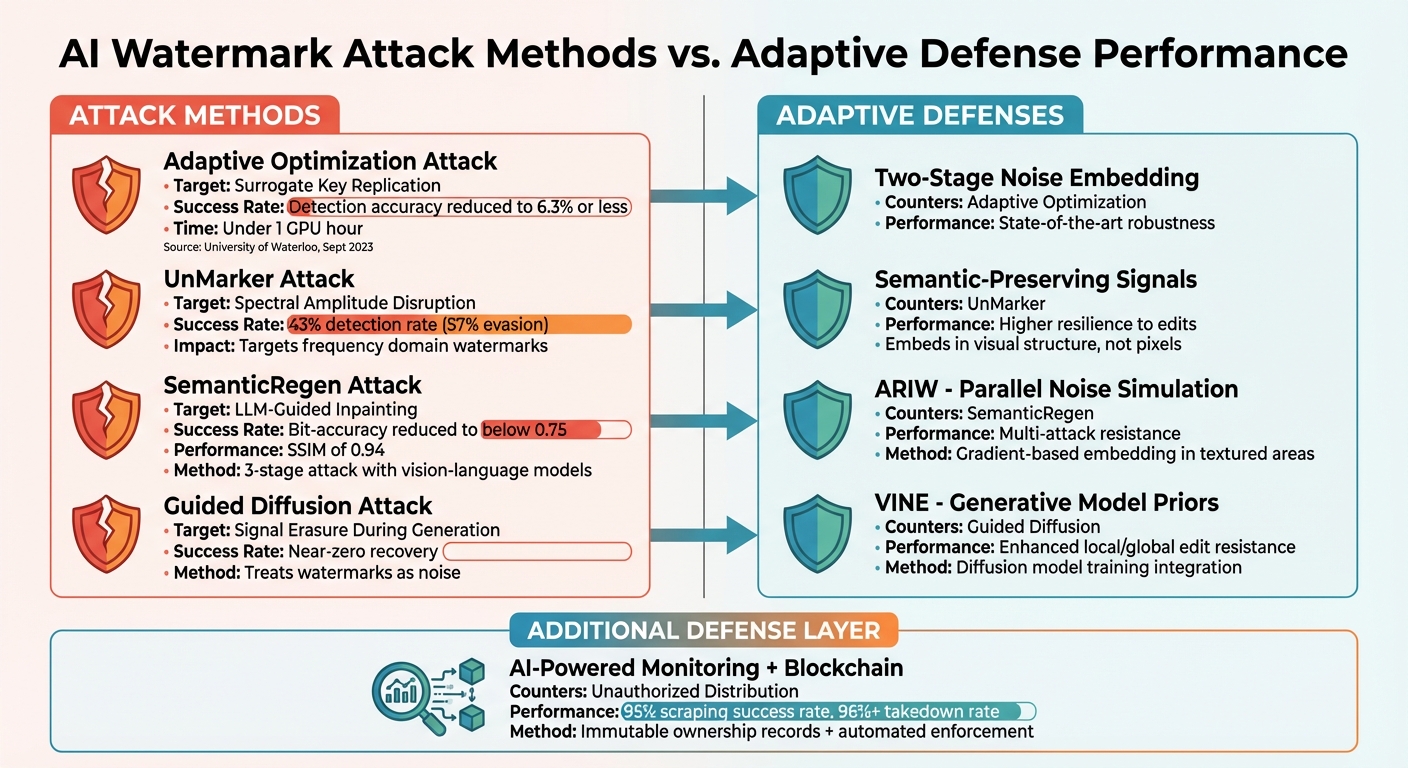
AI Watermark Attack Methods vs Adaptive Defense Performance Comparison
The clash between AI-driven attacks and advanced watermarking defenses has reached a pivotal stage. Recent findings shed light on how traditional watermarking systems are being compromised and the strategies being developed to counteract these sophisticated threats. Let’s dive into some of the most notable attack methods and how adaptive defenses are stepping up to the challenge.
In September 2023, Nils Lukas and his team at the University of Waterloo showcased an Adaptive Optimization Attack targeting Stable Diffusion. By employing differentiable surrogate keys to mimic secret watermarking keys locally, they managed to slash the detection accuracy of five major watermarking techniques to a mere 6.3% or less in under one GPU hour – without causing any visible damage to the images [7]. This experiment underscores how even advanced watermarking technologies can be systematically dismantled with relatively low computational effort.
The stakes were raised even higher in May 2025 when researchers Krti Tallam, Caleb Geniesse, and their colleagues from the University of California, Berkeley, and Stanford University introduced SemanticRegen. This three-stage attack utilized a vision-language model for captioning and an LLM-guided diffusion inpainting process to erase watermarks effectively. Tested across 1,000 prompts, it successfully bypassed the semantic TreeRing watermark and reduced bit-accuracy for StegaStamp and StableSig to below 0.75, achieving an SSIM (structural similarity index measure) of 0.94 [5]. Reflecting on the broader implications of these vulnerabilities, Andre Kassis from the University of Waterloo remarked:
"Defensive watermarking is not a viable defense against deepfakes, and we urge the community to explore alternatives" [4].
In response to these escalating threats, modern adaptive defenses are employing cutting-edge techniques to stay ahead. For example, Adaptive Robust Iterative Watermarking (ARIW) employs parallel noise simulation and gradient-based embedding to maintain its strength against various attack methods [2]. Similarly, frameworks like VINE utilize diffusion model priors to resist both localized and global semantic edits [1]. When combined with blockchain timestamping and advanced monitoring systems, these defenses create robust, multi-layered protection that goes beyond the watermark itself.
Here’s a comparison of attack success rates and the performance of adaptive defenses:
Table: Attack Success Rates vs. Defense Performance
| Attack Method | Target Mechanism | Attack Success Rate | Adaptive Defense | Defense Performance |
|---|---|---|---|---|
| Adaptive Optimization [7] | Surrogate Key Replication | < 6.3% Detection Accuracy | Two-Stage Noise Embedding [10] | State-of-the-art robustness |
| UnMarker [4] | Spectral Amplitude Disruption | 43% Detection Rate | Semantic-Preserving Signals [3] | Higher resilience to edits |
| SemanticRegen [5] | LLM-Guided Inpainting | < 0.75 Bit-Accuracy | Parallel Noise Simulation (ARIW) [2] | Multi-attack resistance |
| Guided Diffusion [1] | Signal Erasure During Generation | Near-Zero Recovery | Generative Model Priors (VINE) [1] | Enhanced local/global edit resistance |
| Unauthorized Distribution | Web-Based Content Theft | N/A | AI-Powered Monitoring + Blockchain | 95% scraping success, 96%+ takedown rate |
This evolving battle between attacks and defenses emphasizes the need for continuous innovation in watermarking and content protection systems. While attackers push the boundaries of AI capabilities, adaptive defenses are rising to meet the challenge with layered and dynamic solutions.
The Future of Watermarking and Content Protection
The world of watermarking is evolving rapidly. Traditional methods that focus on pixel-level alterations are being replaced by semantic-preserving watermarks, which embed protection signals into the very essence of an image’s visual structure. Xuandong Zhao and his research team emphasize this shift:
"Our finding underscores the need for a shift in research/industry emphasis from invisible watermarks to semantic-preserving watermarks" [3].
Next-generation watermarking systems are becoming more advanced, using techniques like adaptive gradient embedding to strategically place watermarks in high-texture areas. These regions are harder for AI to manipulate without degrading the image quality. Frameworks such as ARIW take this a step further by employing parallel noise simulation within encoders. This method allows the system to defend against multiple types of attacks simultaneously, creating a "robust residual" – a watermark pattern that can withstand even the most aggressive AI-driven removal attempts [2].
Another leap forward comes from using generative model priors to enhance watermark durability. Systems like VINE utilize the characteristics of diffusion models during training, embedding watermarks as natural features of the image. This ensures that generative models retain these watermarks to preserve the image’s overall quality [1]. By embedding the watermark as a conceptual element rather than a superficial addition, these methods make it harder to erase while maintaining visual integrity. Such advancements are critical as the volume of AI-generated content continues to grow, creating new challenges for content protection.
Recent data highlights the rising need for reliable and verifiable protection mechanisms.
Looking ahead, the future of watermarking will combine adaptive techniques with stronger verification systems. For instance, integrating blockchain timestamping with semantic watermarks could offer a dual-layer defense. While semantic watermarks make removal difficult, blockchain technology provides immutable proof of ownership and creation dates. Additionally, AI-powered monitoring systems are achieving impressive results, with 95% success rates in detecting unauthorized content and 96%+ takedown rates for verified violations. This multi-faceted approach addresses both the technical hurdles of watermarking and the enforcement challenges of protecting digital assets in an era dominated by AI-generated media.
Conclusion: Protecting Digital Assets from AI Threats
The rise of AI-based attacks has rendered traditional pixel-level watermarks almost useless. Techniques like diffusion-based editing can strip away their embedded data with ease, leaving digital assets vulnerable [1]. The "UnMarker" attack highlights this weakness, dropping the detection rates of even advanced semantic watermarks to a concerning 43% [4]. This reality demands a shift toward more resilient and advanced approaches.
New watermarking methods are stepping up to meet this challenge. By embedding watermarks into intricate textures and employing parallel noise simulation, these techniques aim to endure a variety of attacks [2]. Xuandong Zhao from UC Santa Barbara emphasizes the urgency of this evolution:
"Our finding underscores the need for a shift in research/industry emphasis from invisible watermarks to semantic-preserving watermarks" [3].
A robust defense strategy combines multiple layers of protection. For instance, pairing semantic watermarking with blockchain-enabled timestamping creates a powerful dual-layer system. This approach not only makes watermark removal far more difficult but also provides tamper-proof proof of ownership. At ScoreDetect, our systems have proven their effectiveness, achieving a 95% detection rate and surpassing a 96% takedown rate for violations. This combination of advanced watermarking and blockchain technology equips businesses to tackle AI threats head-on.
Ultimately, the systems that embed protection directly into the content and use adaptable, multi-layered defenses will be the ones that withstand the ever-evolving landscape of AI attacks. As generative AI continues to advance, businesses must act now to implement these forward-thinking, AI-driven protection strategies.
FAQs
How do AI attacks compromise digital watermarking systems?
AI can exploit weaknesses in traditional watermarking techniques by targeting the algorithms that embed hidden marks. For example, attackers might use sophisticated methods to remove or modify watermarks without compromising the content’s quality. Generative AI techniques, such as introducing random noise or reconstructing images, can wipe out as much as 99% of invisible watermarks while maintaining the visual appearance of the original content. Open-source watermarking algorithms face even greater risks, as attackers can analyze and manipulate the hidden patterns to produce convincing counterfeit materials.
To address these challenges, adaptive watermarking technologies are becoming crucial. These systems use dynamic embedding strategies combined with cryptographic verification to strengthen defenses. Platforms like ScoreDetect offer advanced solutions to protect digital assets from AI-driven tampering and forgery, ensuring their integrity and security.
How can watermark protection be improved to counter AI-based attacks?
AI-powered attacks have exposed the weaknesses of traditional invisible watermarks, pushing researchers to create smarter, more resilient solutions. One such approach is adaptive watermarking, which tweaks the embedding strength based on the unique features of an image. This method helps watermarks withstand noise and distortion while keeping the image’s quality intact. Even with advanced AI removal techniques, these watermarks are designed to stay in place.
Another breakthrough is semantic watermarking, where the watermark is linked to the content of the image itself. Removing these marks without changing the image’s meaning becomes a tricky challenge, making them particularly effective against regeneration attacks. For AI-generated content, token-level watermarking steps in by embedding marks directly within the data structure. This ensures the watermark remains intact, even after compression or other transformations.
ScoreDetect uses these advanced techniques to deliver invisible, non-intrusive watermarking solutions. By staying ahead of evolving threats, it ensures your digital assets are safeguarded effectively.
How does blockchain improve the security of digital assets?
Blockchain boosts the security of digital assets by establishing an unchangeable record of cryptographic hashes, such as SHA-256, for watermarked content. This makes it easy to spot any attempts at tampering, offering reliable proof of authenticity and verification.
Instead of storing the actual digital assets, blockchain preserves cryptographic proofs on a decentralized ledger. This method reinforces copyright protections and ensures that ownership rights are secure and easily verifiable for the long term.

