Audio watermarking is the process of embedding hidden signals into audio files to protect copyright and prove ownership. Detection tools extract these signals to verify authenticity, even without the original file.
This technology is crucial in combating piracy, AI-generated content misuse, and unauthorized distribution. Here’s what you need to know:
- How It Works: Psychoacoustic watermarks are embedded into the audio’s waveform or spectral properties, remaining intact through playback, copying, or compression. Detection uses algorithms to extract and confirm these signals.
- Why It Matters: With advanced editing tools and AI-generated content on the rise, watermarking helps creators prove ownership, track misuse, and protect intellectual property.
- Key Challenges: Compression, noise, and AI-based evasion techniques can degrade watermarks, but advanced methods like wavelet-domain techniques and redundant embedding improve reliability.
- Applications: From streaming platforms and broadcasters to legal disputes and AI safety, watermarking plays a critical role in protecting digital audio assets.
Detection systems like ScoreDetect enhance protection with invisible watermarking, blockchain verification, and automated takedowns, making them vital for safeguarding audio content in today’s digital landscape.
AI Music Copyright: The Watermarking Solution Explained
sbb-itb-738ac1e
How Audio Watermark Detection Works
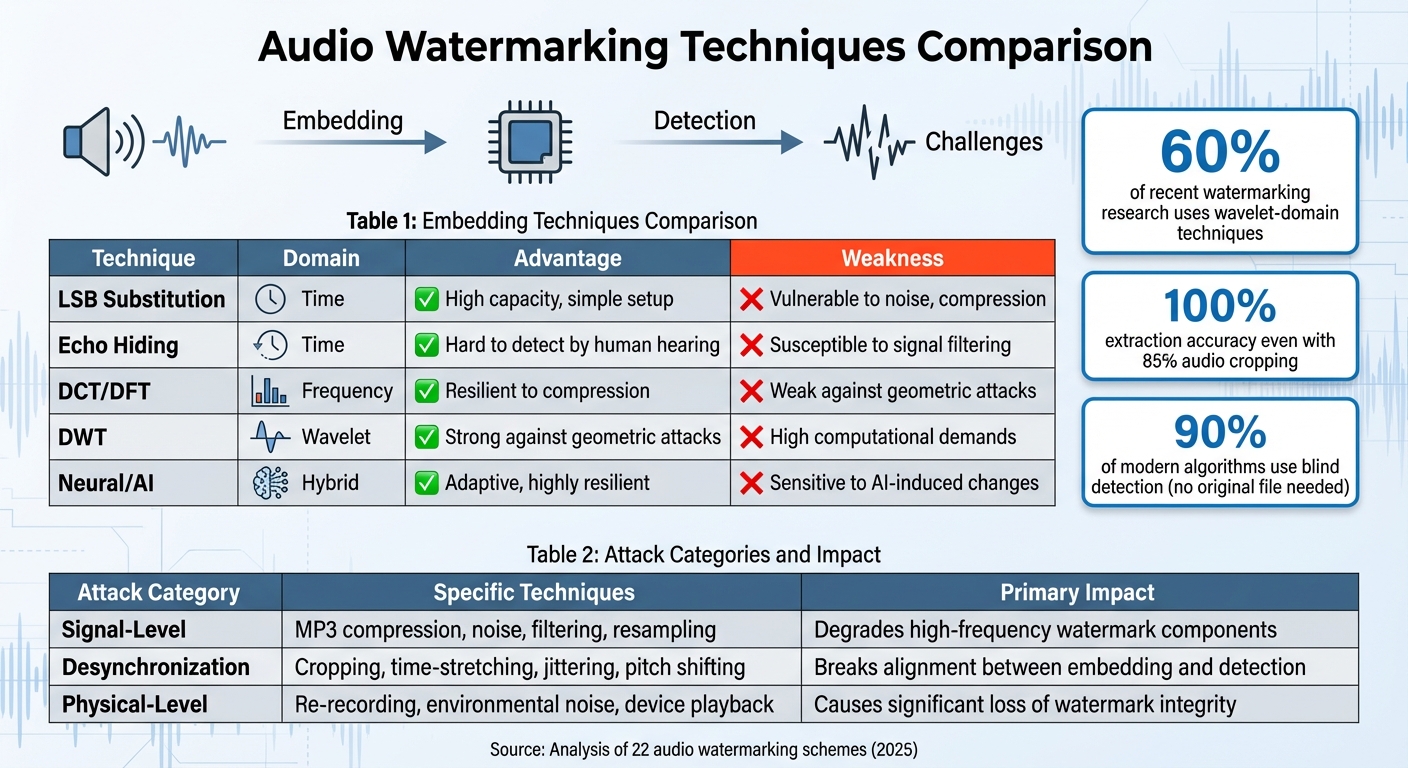
Audio Watermarking Techniques: Comparison of Embedding Methods and Attack Resistance
Audio watermark detection involves embedding a watermark into a file and later extracting it using algorithms that operate across both time and frequency domains.
Embedding and Extracting Watermarks
Watermarks can be embedded through time-domain methods like Least Significant Bit (LSB) substitution or echo hiding. These methods are straightforward to implement but are more vulnerable to compression and noise. On the other hand, transform-domain techniques provide stronger protection by converting the audio signal into a frequency or spectral form – using transforms such as Discrete Cosine Transform (DCT), Discrete Wavelet Transform (DWT), or Short-Time Fourier Transform (STFT) – and embedding watermark bits into the transformed coefficients before converting the signal back [8][4][6].
Interestingly, studies show that wavelet-domain techniques are used in about 60% of recent watermarking research because they strike a better balance between being hard to detect and maintaining audio quality [2].
To ensure reliability, redundancy is embedded across multiple audio frames. This approach can achieve 100% extraction accuracy even when up to 85% of the watermarked audio is cropped, eliminating the need for synchronization codes [6].
Detection methods fall into two categories: blind and non-blind. Blind detection, used in 90% of modern algorithms, does not require the original audio file, making it ideal for real-world copyright applications [2]. Non-blind detection, while requiring the original file, offers greater reliability in forensic investigations [8][9]. As noted in Lossless Information Hiding in Images (2017):
"A watermark is not transmitted in addition to a digital signal, but rather as an integral part of the signal samples." [9]
These techniques form the foundation for robust watermark detection, which is explored further in the next section.
Technologies Used in Detection
Detection systems often rely on correlation-based schemes, which measure the similarity between the analyzed signal and a known watermark pattern. If the correlation exceeds a set threshold, the watermark is confirmed [9]. AI-driven systems take this further, using trained decoder networks to analyze audio features and reconstruct the original watermark bit-string through techniques like linear layers or average pooling [6].
The choice of embedding technique plays a critical role in detection reliability. For instance, Quantization Index Modulation (QIM) modifies the host signal differently for "0" and "1" bits, offering strong resistance to distortion [2]. DCT-based methods excel against MP3-style compression, while DWT methods are better at withstanding geometric attacks, though they require more computational power [8][9].
| Technique | Domain | Advantage | Weakness |
|---|---|---|---|
| LSB Substitution | Time | High capacity, simple setup | Vulnerable to noise, compression |
| Echo Hiding | Time | Hard to detect by human hearing | Susceptible to signal filtering |
| DCT/DFT | Frequency | Resilient to compression | Weak against geometric attacks |
| DWT | Wavelet | Strong against geometric attacks | High computational demands |
| Neural/AI | Hybrid | Adaptive, highly resilient | Sensitive to AI-induced changes |
Traditional systems often use synchronization codes to locate the watermark’s starting point. However, modern AI-based methods embed watermarks redundantly across the entire audio file, making them resistant to desynchronization attacks like cropping, time-stretching, or jittering, which aim to disrupt the watermark’s position [6].
Challenges in Audio Watermark Detection
Even the most advanced watermarking systems encounter hurdles when applied in practical settings. A large-scale 2025 study analyzing 22 audio watermarking schemes revealed that none could withstand all real-world distortions [4]. This highlights the delicate balance watermarks must achieve between being imperceptible, robust, and capable – often referred to as the "Magic Triangle" – to endure unpredictable attacks [2][4]. The following sections explore how these trade-offs are tested by both traditional signal distortions and modern AI-based evasion techniques. Let’s dive into the specific challenges watermark detection faces.
Signal Distortion Attacks
Signal distortions are among the most common threats to watermark detection. These include processes like MP3 compression, Gaussian noise addition, low-pass filtering, resampling, and quantization [4]. Each of these can degrade or even erase the embedded watermark patterns.
Desynchronization attacks introduce an even tougher challenge. Techniques such as cropping, time-scale modification (TSM), jittering, and pitch shifting disrupt the synchronization between the watermark embedding and its detection mechanism [6]. By breaking this alignment, these attacks make it difficult to extract the watermark accurately.
Physical-level distortions add yet another layer of complexity. When audio is played through speakers and re-recorded – often called the "acoustic path" – the combination of environmental noise and hardware limitations can severely degrade the watermark signal [4]. This makes digital content protection for audio in scenarios like concerts, broadcasts, or public events especially difficult.
| Attack Category | Specific Techniques | Primary Impact |
|---|---|---|
| Signal-Level | MP3 compression, noise, filtering, resampling | Degrades high-frequency watermark components |
| Desynchronization | Cropping, time-stretching, jittering, pitch shifting | Breaks alignment between embedding and detection |
| Physical-Level | Re-recording, environmental noise, device playback | Causes significant loss of watermark integrity |
To combat these challenges, several strategies have been developed. One approach is frame-wise broadcast embedding, which embeds the entire watermark into each audio frame rather than spreading it across the file. This method is particularly effective against cropping attacks [6].
Another key tactic involves domain selection. For example, embedding watermarks in the approximation coefficients of the Discrete Wavelet Transform (DWT) helps protect against MP3 compression, as this process primarily affects high-frequency components [2]. To address time-scale modifications, systems can employ Dynamic Time Warping (DTW) during detection, aligning the distorted signal with the original watermark [3].
While these methods address many signal-level challenges, the rise of AI-based evasion techniques has introduced a new and formidable set of threats.
AI-Based Evasion Techniques
Generative AI has opened the door for attackers to use tools like Voice Conversion and Text-to-Speech models to recreate original audio without its embedded watermark [4]. Additionally, AI models often rely on audio tokenizers – such as Encodec – to compress audio into discrete tokens, effectively erasing watermark patterns. Research has shown that detection accuracy can plummet to 0.5742 (with 0.5 being random guessing) when watermarked audio is processed through the Encodec32 tokenizer, as used in generative tools like MusicGen [5].
Kosta Pavlović, Lead Researcher at DeepMark, emphasizes the challenge:
"Audio watermark decoders require architectural mechanisms that are intrinsically robust to common edits and temporal misalignments. If the architecture is not inherently robust, no amount of augmentation or attack-layer engineering will make training reliably effective." [10]
The problem is compounded by the fact that many deep-learning-based watermarking systems are tailored to specific simulated distortions. AI-based evasion techniques, however, can produce entirely new, out-of-distribution perturbations that these systems fail to recognize, escalating the ongoing battle between watermark developers and attackers.
To address these AI-driven threats, developers are turning to adversarial optimization during the embedding process. This method strengthens watermarks against potential AI alterations. Another promising approach involves Mel-domain detection, as many AI vocoders and synthesis pipelines operate in the Mel-spectrogram space [10]. Using Mel-based detectors significantly improves watermark resilience against voice cloning.
Multi-watermarking is also gaining traction. By embedding the watermark multiple times, detection accuracy can improve from 0.57 to 0.89, though this comes with a noticeable trade-off in audio quality [5].
Applications of Audio Watermark Detection
Audio watermark detection is widely used across various industries to safeguard intellectual property, verify content authenticity, and ensure compliance with legal standards.
Media and Entertainment Industry
The media and entertainment sector faces ongoing challenges like piracy and unauthorized content redistribution. Audio watermarking offers a robust solution by enabling platforms to screen and verify content efficiently – even without access to the original, unwatermarked version.
Streaming platforms, for instance, employ "takedown gates" to filter uploads during the ingest process. A standout example is the HashWave system, which uses multi-feature audio hashing to achieve an impressive AUC of 0.957, even against heavily transformed audio [3]. This level of precision helps identify manipulated or unauthorized content.
Broadcast networks also rely on watermarking to maintain control over distributed content. As Carlos Jair Santin-Cruz, a Ph.D. researcher in Digital Signal Processing, explains:
"Audio watermarking has been introduced to give authors and owners control over the use of audio signals" [2].
Embedded watermarks allow broadcasters to track unauthorized transmissions, ensuring accurate royalty payments and billing.
The rise of generative AI has further underscored the importance of watermarking. A growing trend is "user-level watermarking", where individual creators embed marks into their audio before sharing it online. This ensures that if the audio is later used to train AI models, the generated outputs carry a traceable watermark [4].
Podcasting platforms are also leveraging watermarking to manage User-Generated Content (UGC). By using perceptual hashing, they can detect near-duplicate audio segments, even if the content has been edited, helping to curb unauthorized redistributions [3].
| Application Category | Primary Function | Key Benefit |
|---|---|---|
| Copyright Protection | Proving ownership and blocking unauthorized use | Provides evidence in ownership disputes |
| Monitoring | Collecting broadcast data for billing | Ensures compliance with royalty agreements |
| Content Management | Automating deduplication and access control | Enforces licensing terms at scale |
| AI Safety | Detecting deepfakes and voice cloning | Protects against synthetic impersonation risks |
Legal and Compliance Enforcement
Audio watermarking also plays a critical role in legal and compliance scenarios. Unlike metadata, which can be stripped away, watermarks are embedded in the audio waveform, making them resilient to editing and distribution. This makes them indispensable in intellectual property disputes, offering verifiable proof of authenticity and tampering [2].
The technology is also a powerful tool against AI-driven voice fraud. In one notable case, scammers used a deepfake of a CEO’s voice to deceive an employee into transferring $243,000 to a fraudulent account [4]. Highlighting the growing risks, researcher Robin San Roman notes:
"In the rapidly evolving field of speech generative models, there is a pressing need to ensure audio authenticity against the risks of voice cloning" [1].
Blockchain-integrated watermarking adds another layer of security. By combining perceptual hashing with blockchain networks like Ethereum and decentralized storage solutions such as IPFS, organizations can establish tamper-proof records of content usage. Blockchain-based systems have demonstrated efficiency, with contract execution times averaging just 0.044 seconds [3].
Platforms like ScoreDetect take this a step further. By using invisible watermarking and blockchain timestamping, ScoreDetect creates verifiable proof of ownership without storing the actual audio file. This is particularly useful in legal proceedings. The platform also automates takedown notices, achieving a 96% success rate in removing unauthorized content. These features make it invaluable for media companies, legal teams, and content creators seeking to protect their intellectual property.
Financial institutions and government agencies are increasingly adopting watermark detection to authenticate audio recordings used as evidence. As voice synthesis technology becomes more sophisticated, distinguishing genuine recordings from AI-generated forgeries is crucial. However, as Yizhu Wen from the University of Hawaii at Manoa cautions:
"Watermarking may not be a viable long-term IP protection strategy, as it cannot be modified or ‘patched’ once deployed" [4].
For now, though, watermarking remains one of the most effective tools for proving ownership and detecting unauthorized use in both media and legal contexts.
Using ScoreDetect for Audio Watermark Detection
ScoreDetect offers a robust solution for safeguarding audio content against unauthorized use and piracy. By combining invisible watermarking, automated detection, and blockchain verification, it provides a layered defense system that spans the entire lifecycle of content protection – from prevention to enforcement.
ScoreDetect Features
ScoreDetect tackles challenges like signal distortion and AI-based evasion with invisible watermarking that remains intact through processes like MP3 compression, pitch shifting, and time stretching. Using multi-feature perceptual hashing, it creates unique audio fingerprints by combining elements like MFCC, chroma, CQT, and spectral contrast. This approach captures both harmonic and temporal patterns, making it incredibly tough for signal processing techniques to bypass detection [3].
The platform also leverages parallelized extraction, increasing processing speeds by up to 90% when using 16 cores [7]. Blockchain timestamping further ensures tamper-proof ownership records without storing the actual audio, with contract execution times averaging just 0.044 seconds [3]. This efficiency allows ScoreDetect to monitor up to 1.5 billion suspicious links monthly across web platforms, IPTV, and mobile apps [11].
In terms of enforcement, ScoreDetect achieves a 96% success rate in takedowns [11]. When unauthorized content is found, it automatically sends legally compliant delisting notices to hosting providers, search engines, and social media platforms. For live events like sports or concerts, the system can identify and block unauthorized re-streaming sources within seconds [11].
These advanced features translate into real business value, offering substantial protection and operational efficiency.
Business Benefits of ScoreDetect
ScoreDetect helps media companies and content creators reclaim revenue by disrupting illegal distribution and converting viewers of pirated material into paying subscribers [11]. It also ensures compliance with the security standards of major entities like Hollywood studios and international sports leagues [11].
Automation enhances operational efficiency, with intelligent web scraping achieving a 95% success rate in bypassing preventive measures. This streamlines the entire enforcement workflow – from discovery to takedown – allowing legal teams to focus on higher-level tasks.
The platform’s perceptual hashing framework is highly effective, with an AUC of 0.957 in detecting piracy across more than twenty signal-processing transformations [3]. This reduces false positives while ensuring genuine infringements are accurately identified.
ScoreDetect Use Cases
Media and Entertainment: Companies use ScoreDetect to protect music releases, podcasts, and audiobooks. For live events, dynamic watermarking identifies specific leak sources in real time [11]. The WordPress plugin adds another layer of protection, using blockchain timestamping to enhance SEO by boosting E-E-A-T signals.
Marketing and Advertising: Agencies safeguard proprietary audio assets like jingles and voice-overs. With integrations across over 6,000 web apps via Zapier, workflows become fully automated.
Legal and Law Firms: ScoreDetect’s forensic tools authenticate audio evidence and establish a secure chain of custody. As voice synthesis technology evolves, the platform’s watermarking and blockchain verification ensure defensible records for court cases, distinguishing genuine recordings from AI-generated ones.
Academic Institutions: The platform helps combat audio plagiarism in assignments, offering immutable blockchain timestamps to support academic integrity proceedings.
Finance, Healthcare, and Government: Sensitive audio recordings are protected, ensuring compliance with data protection standards. ScoreDetect integrates seamlessly into existing security systems, making it a versatile tool for these sectors.
Conclusion
Protecting audio content through watermark detection has become a cornerstone of copyright enforcement in the digital age. Embedding watermarks directly into the audio waveform offers a more robust defense against tampering compared to methods like metadata tagging [4]. With nearly 90% of modern algorithms using blind detection, this approach has proven to be both practical and scalable for rights holders [2].
As technology advances, the risks to audio content are growing. AI-generated songs that imitate well-known artists and deepfake voice scams – such as the case where fraudsters stole $243,000 – illustrate the pressing need for stronger intellectual property safeguards [4]. These examples emphasize the importance of verifying ownership and provenance to support legal action and prevent fraud.
"The expeditious extraction of watermarks plays a crucial role in deterring piracy and curtailing unauthorized distribution of copyrighted content. It strengthens the ability to promptly identify infringements and take necessary legal actions." – Scientific Reports [7]
ScoreDetect addresses these challenges by combining invisible watermarking, blockchain-based verification, and automated enforcement tools. This system not only shields audio content from piracy but also provides a reliable way to prove ownership and take swift action when rights are violated.
FAQs
How does audio watermarking help protect against misuse of AI-generated audio?
Audio watermarking is an effective way to safeguard against the misuse of AI-generated audio. It works by embedding invisible, tamper-resistant markers directly into audio files. These markers remain intact even if the audio undergoes modifications or processing, making them a reliable tool for verifying ownership and authenticity.
This technology plays a critical role in addressing challenges like voice cloning and the creation of synthetic audio that mimics real voices. By embedding watermarks either during the audio creation process or directly into the files, content creators can establish ownership and protect their intellectual property. In a time when AI tools are advancing rapidly, audio watermarking offers a dependable method to keep content secure.
What challenges are involved in protecting audio watermarks from tampering?
Protecting audio watermarks from tampering is no small feat. The biggest hurdle? Ensuring they can withstand signal processing attacks and transformations. Everyday operations like compression, filtering, resampling, cropping, or even adding noise can easily distort or strip away watermarks. This makes verifying the authenticity of audio content a tricky task. And with AI-powered attacks now in the mix, the challenge grows even more complex, as these tools can introduce sophisticated methods to corrupt or erase watermarks entirely.
Another major challenge lies in striking the right balance between imperceptibility and robustness. Watermarks need to be subtle enough that listeners don’t notice them, yet tough enough to endure various modifications. Techniques like embedding watermarks in frequency domains can improve durability, but they often come with a trade-off: a potential dip in audio quality. The key to preserving both the watermark and the original sound? Constant innovation to stay ahead of evolving threats.
How does ScoreDetect protect audio content from unauthorized use?
ScoreDetect protects audio content using invisible, non-disruptive watermarking that guards against illegal use without impacting the listening experience. This technology is paired with intelligent web scraping and content analysis to identify when and where your content is being misused.
When unauthorized usage is detected, ScoreDetect can automatically issue takedown notices, ensuring quick removal of infringing material. This streamlined process makes safeguarding your intellectual property straightforward and efficient.

