Data encryption is a key tool for meeting privacy law requirements. It protects sensitive information by converting it into unreadable code, ensuring security during storage and transmission. Here’s why encryption matters:
- GDPR: Recognizes encryption as an "appropriate measure" for protecting personal data. If encrypted data is stolen but remains unreadable, breach notifications may not be required.
- CCPA/CPRA: While encryption isn’t explicitly mandated, it supports compliance by demonstrating "reasonable security practices."
- HIPAA: Requires encryption for healthcare data leaving secure networks, with strict standards for protecting sensitive health information.
Key encryption methods include AES-256 for data at rest and TLS 1.3 for data in transit. Proper key management, multi-factor authentication, and regular reviews are essential for maintaining compliance.
This guide explains how encryption aligns with privacy laws, explores practical strategies for implementation, and highlights challenges organizations face in securing data. By combining encryption with tools like blockchain verification and automated workflows, businesses can meet current legal standards and prepare for future regulations.
What Are Legal Obligations For Encrypting Sensitive Data At Rest?
Privacy Laws and Their Encryption Requirements
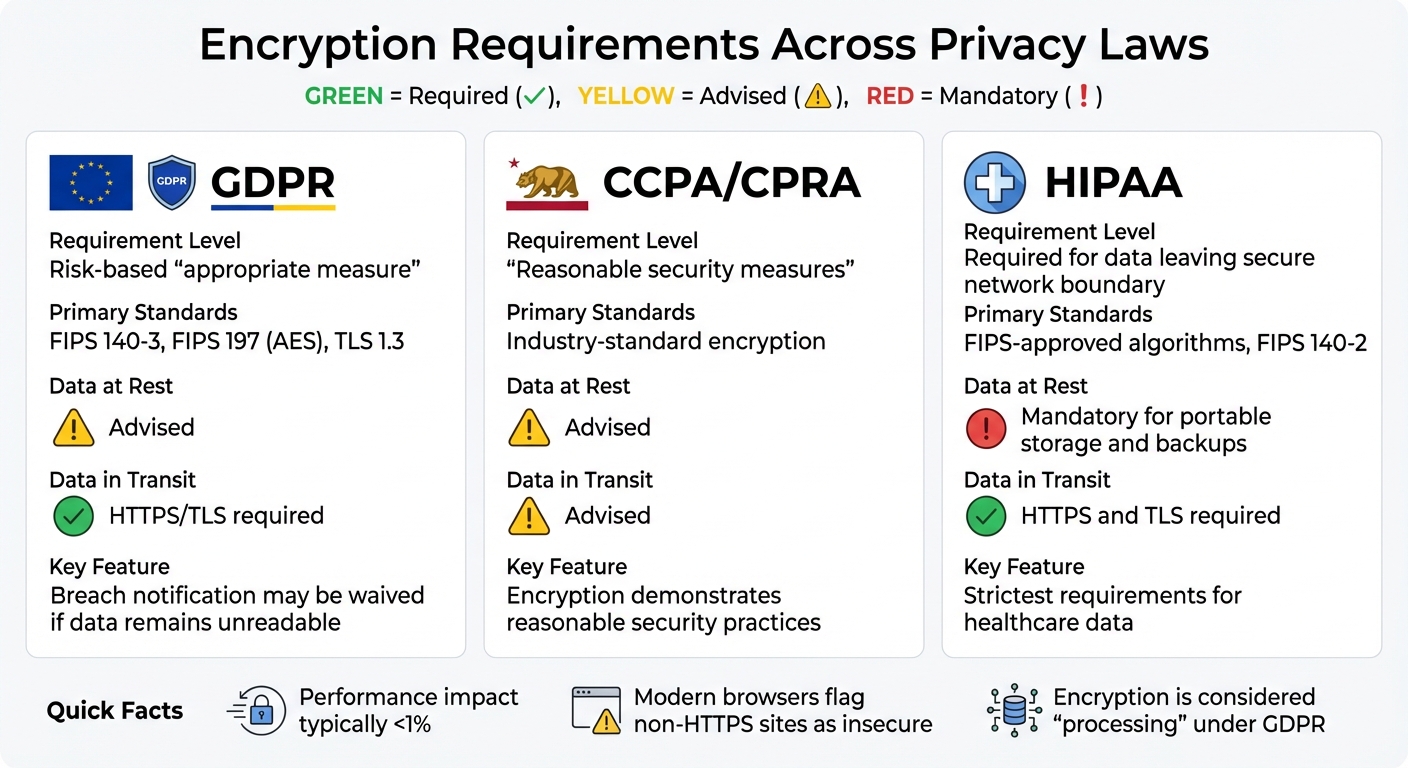
GDPR, CCPA, and HIPAA Encryption Requirements Comparison Chart
Various privacy regulations approach encryption differently, but they all recognize its role in safeguarding sensitive data. Knowing the specific encryption requirements of each law is essential for developing a compliant security strategy. Let’s explore how GDPR, CCPA/CPRA, and HIPAA address encryption.
GDPR: EU Encryption Standards
Article 32 of the GDPR identifies encryption as an "appropriate technical and organisational measure" for protecting personal data. The Information Commissioner’s Office (ICO) advises that these measures should align with the nature of the data, associated risks, and implementation costs [1][2]. Organizations are expected to secure data both when stored (data at rest) and when transferred across networks (data in transit). Notably, if encrypted data is stolen but remains unreadable, breach notification requirements may be waived.
Under GDPR, encryption itself is considered a form of data processing because it modifies personal information. To meet GDPR standards, organizations are encouraged to use frameworks like FIPS 197 (AES) and FIPS 140-3.
While GDPR emphasizes risk-based measures, U.S. regulations take a slightly different approach, focusing on reasonable security practices.
CCPA and CPRA: California Data Security
The California Consumer Privacy Act (CCPA) and its updated version, the California Privacy Rights Act (CPRA), require businesses to implement "reasonable security procedures and practices" to protect personal data. Although encryption isn’t explicitly mandated, it can serve as a strong indicator of reasonable security. Encrypting sensitive data both at rest and in transit is a practical way to demonstrate compliance with these laws.
In sectors like healthcare, encryption isn’t just a best practice – it’s a regulatory requirement under HIPAA.
HIPAA: Healthcare Data Protection
HIPAA’s Security Rule takes a more detailed approach to encryption, particularly for healthcare organizations. According to the CDC, encryption ensures that only authorized individuals can access sensitive data [3]. HIPAA mandates that any digital communications or storage media containing protected health information (PHI) must be encrypted when leaving a secure network. This includes web traffic, emails, portable drives, and backups.
Healthcare providers are advised to use FIPS-approved algorithms and comply with FIPS 140-2 standards for encryption. Data in transit should be secured using HTTPS and valid security certificates.
Comparing Encryption Requirements
Here’s a quick comparison of encryption standards across these regulatory frameworks:
| Regulation | Requirement Level | Primary Standards | Data at Rest | Data in Transit |
|---|---|---|---|---|
| GDPR | Risk-based "appropriate measure" | FIPS 140-3, FIPS 197 (AES), TLS 1.3 | Advised | HTTPS/TLS required |
| CCPA/CPRA | "Reasonable security measures" | Industry-standard encryption | Advised | Advised |
| HIPAA | Required for data leaving secure network boundary | FIPS-approved algorithms, FIPS 140-2 | Mandatory for portable storage and backups | HTTPS and TLS required |
Practical Considerations
Encryption typically impacts system performance minimally – often just a fraction of a percent – so end users rarely notice any slowdown [3]. Additionally, modern web browsers now flag websites as "insecure" if HTTPS isn’t used, highlighting the importance of encrypting data in transit [1].
Encryption Methods for Regulatory Compliance
Once you know what privacy laws require, the next step is selecting encryption methods that meet those standards. Today’s encryption technology offers powerful protection without significantly affecting system performance [3]. Let’s break down some key methods that help ensure both confidentiality and integrity while staying compliant with privacy laws.
End-to-End Encryption and AES-256
The Advanced Encryption Standard (AES-256) is widely regarded as the benchmark for securing data at rest. Approved under FIPS 197, AES-256 replaced the older and less secure Data Encryption Standard (DES) [5]. With around 10^78 possible key combinations, brute-forcing AES-256 is computationally out of reach with current technology [5].
For data in transit, TLS 1.3 is the go-to protocol, offering robust security while addressing vulnerabilities found in older SSL versions [1]. Meanwhile, End-to-End Encryption (E2EE) ensures that only the sender and the intended recipient can access the data, blocking unauthorized intermediaries from reading it [3].
"Encryption is a critical component of data security. It ensures that, if the data are accessed by an unauthorized person, they will not be able to read or misuse the data." – Centers for Disease Control and Prevention (CDC) [3]
Portable devices, often vulnerable to theft or loss, benefit from full disk and file-level encryption. For example, HIPAA mandates the use of FIPS-approved encryption for safeguarding such storage [1][3]. However, encryption is only as strong as its key management. Storing encryption keys alongside encrypted data weakens security – using Hardware Security Modules (HSMs) and regularly rotating keys can mitigate this risk [1][2].
Blockchain Timestamping for Data Integrity
Encryption focuses on confidentiality, but ensuring data integrity requires additional measures. This is where blockchain timestamping comes in – it verifies that data hasn’t been altered. Under GDPR Article 5(1)(f), organizations are required to maintain both the "integrity and confidentiality" of personal data [2]. Blockchain achieves this by recording tamper-evident checksums of content without storing the actual data.
"You could include integrity checks alongside encryption to ensure that attackers cannot tamper with encrypted data, even if they are unable to steal it." – Information Commissioner’s Office (ICO) [2]
Pairing blockchain with digital watermarking can also establish proof of ownership for copyrighted materials. For instance, Apple’s iTunes store uses its "FairPlay" Digital Rights Management (DRM) technology to encrypt media files, controlling access while protecting against unauthorized distribution [4]. This approach not only supports copyright compliance but also tracks misuse effectively.
To stay ahead of evolving threats, organizations should conduct annual reviews of their encryption and integrity protocols. Keeping an up-to-date inventory of cryptographic tools ensures a quick response if vulnerabilities are discovered [5].
Multi-Factor Authentication with Encryption
Encryption works best when combined with strong access controls. That’s where Multi-Factor Authentication (MFA) comes into play. By adding a second layer of verification, MFA ensures that even if encryption keys are compromised, unauthorized users can’t access sensitive data [6].
Using Role-Based Access Control (RBAC) and the principle of least privilege further limits access to decryption keys, ensuring they are only available to authorized personnel [2]. With nearly 80% of the global population now covered by privacy laws, and penalties such as Meta’s $1.3 billion GDPR fine in 2022, the importance of proper encryption and access control has never been greater [6].
For government-related compliance, ensure encryption solutions meet FIPS 140-2 or 140-3 standards [1][3]. Automated classification tools can also help identify sensitive data, like PII or PHI, so the appropriate level of encryption is applied [6].
sbb-itb-738ac1e
How to Implement Encryption: Best Practices and Common Challenges
Implementing encryption requires thoughtful planning and consistent oversight. Organizations often face hurdles like managing encryption keys, dealing with outdated technology, and selecting the right tools [2][5]. A structured approach can help navigate these challenges effectively. Below are some practical steps to address common pitfalls.
Data Mapping and Impact Assessments
Before diving into encryption, it’s crucial to understand what data needs protection and why. Conducting a Data Protection Impact Assessment (DPIA) helps identify sensitive information such as personally identifiable information (PII) or protected health information (PHI). This process lays the groundwork for creating a formal encryption policy and maintaining a cryptographic inventory for regular reviews [2].
By mapping your data accurately, you can pinpoint what requires encryption, ensuring your efforts align with compliance standards. This inventory also simplifies the transition to updated encryption methods if a current solution is compromised [5].
"Taking into account the state of the art, the costs of implementation, and the nature, scope, context and purposes of processing… the controller and the processor shall implement appropriate technical and organisational measures to ensure a level of security appropriate to the risk, including… encryption of personal data." – UK GDPR Article 32 [2]
It’s important to remember that encryption is legally classified as a form of "processing" under the UK GDPR because it involves altering data. Consequently, encryption practices must adhere to broader data protection principles like transparency and accountability [2].
Third-Party Vendor Compliance Management
Your encryption strategy isn’t complete without ensuring external vendors meet the same security standards. Sharing data with third parties still leaves you responsible for its protection, so verifying their encryption practices is essential.
Start by confirming that vendors use encryption solutions adhering to recognized industry standards, such as FIPS 197 (AES) or FIPS 140-3 for cryptographic modules [1]. For data in transit, ensure they use TLS 1.3, avoiding outdated protocols [1]. Vendors certified by trusted organizations, like the NCSC’s Certified Assisted Products Scheme (CAPS), should be prioritized [1].
Contracts with vendors should include explicit clauses about key management. A lost decryption key could result in a personal data breach, as it may lead to the accidental loss or unavailability of data [2]. To minimize risks, encourage the use of Hardware Security Modules (HSMs) for key storage and enforce least privilege access policies. Regular reviews of vendor tools – ideally conducted annually – help ensure they remain effective against new threats [5].
Incident Monitoring and Response
Even with robust encryption in place, ongoing monitoring is essential to identify vulnerabilities and respond to incidents. Subscribing to security alerts can provide updates on encryption methods and their effectiveness [5]. For example, the Data Encryption Standard (DES), once widely used, became obsolete in the late 1990s when it could be cracked in under 24 hours [5].
Develop a clear update plan to transition to new encryption methods if an existing solution is compromised. This plan should outline steps for re-encrypting data, revoking outdated keys, and notifying affected parties when necessary. Effective encryption can sometimes relieve you from notifying individuals in the event of a breach – provided the data is unreadable to unauthorized users [2].
"If you lose a decryption key it means that no-one, including you, is able to decrypt the data… loss of a decryption key may constitute ‘accidental loss, destruction or damage’ to personal information." – Information Commissioner’s Office (ICO) [2]
To strengthen your defenses, combine encryption with additional security measures like Role-Based Access Control (RBAC) and integrity checks. Encryption alone isn’t enough if devices are left unlocked or if metadata and DNS queries remain exposed during transit [1]. By layering multiple protections, you create a more resilient "defense in depth" strategy. Together with strong internal policies, these measures form a comprehensive encryption framework that supports compliance and safeguards against evolving threats.
How ScoreDetect Supports Privacy Law Compliance
Achieving compliance with privacy laws goes beyond just encrypting data – it requires a thoughtful approach to safeguarding digital content at every stage of its lifecycle. ScoreDetect tackles these challenges with a mix of blockchain verification, invisible watermarking, and automated workflows, all tailored to meet the unique needs of industries like healthcare, finance, and digital media.
Blockchain Checksum Technology for Copyright Protection
ScoreDetect leverages blockchain checksum technology to align with regulations like GDPR, CCPA, and HIPAA. By storing cryptographic hashes on the blockchain while keeping sensitive data off-chain, the platform creates an immutable audit trail without compromising the flexibility to delete or modify original data. This approach satisfies GDPR’s "Right to be Forgotten" while maintaining the integrity required by privacy laws.
This method also serves as a pseudonymization technique under GDPR and CCPA, minimizing the exposure of raw personal data on public ledgers. With its tamper-proof records, ScoreDetect ensures that unauthorized changes to healthcare or financial documents are immediately detectable, addressing HIPAA’s stringent data integrity requirements.
A real-world example of this approach is Estonia’s e-Health system, which uses KSI Blockchain to secure access logs while keeping patient records in traditional databases. Similarly, Medicalchain employs Hyperledger Fabric for permissioned blockchain architecture, enabling secure collaboration and compliance with patient privacy regulations.
Invisible Watermarking and Workflow Automation
To complement encryption, ScoreDetect employs invisible watermarking for continuous traceability of digital assets. This ensures that even after authorized access, content remains protected and traceable. While encryption secures data at rest and during transit, watermarking safeguards it throughout its lifecycle, addressing UK GDPR’s requirement to prevent "unauthorized or unlawful processing and accidental loss."
ScoreDetect’s watermarking integrates with over 6,000 web apps, enabling automated workflows to meet emerging regulations like the 2025 TAKE IT DOWN Act. For instance, its WordPress plugin automatically captures and verifies every article published or updated, creating blockchain-based proof of ownership. This feature not only enhances compliance but also boosts SEO by aligning with Google’s E-E-A-T guidelines (Experience, Expertise, Authoritativeness, and Trustworthiness).
This dual approach of watermarking and automation supports the regulatory principle outlined in Article 32 of the UK GDPR:
"Taking into account the state of the art… the controller and the processor shall implement appropriate technical and organisational measures to ensure a level of security appropriate to the risk."
By combining encryption with persistent ownership tracking, ScoreDetect helps organizations meet these evolving security standards.
Enterprise Features for Regulatory Compliance
Beyond its technical capabilities, ScoreDetect’s Enterprise plan offers advanced features like 24/7 monitoring, automated takedowns with a 96% success rate, and dedicated support. These tools are crucial for meeting the stricter requirements under HIPAA and the Digital Operational Resilience Act (DORA), which mandate encryption and other security measures starting in 2025.
For healthcare organizations, ScoreDetect simplifies compliance with the 2025 HIPAA mandate for multi-factor authentication and annual penetration testing. Its automated workflows also enable continuous vulnerability scanning, which became mandatory in January 2025. As Melanie Fontes Rainer, Director of the Office for Civil Rights, emphasized:
"Voluntary cybersecurity goals are no longer sufficient to drive the behavioral change needed across the healthcare sector."
In financial services, where breach costs average $6.08 million – 22% higher than the global average – ScoreDetect’s combination of blockchain checksums, watermarking, and automated monitoring helps meet DORA’s "future-resilient" encryption standards. The platform also generates formal recognition certificates and maintains an unlimited revision history, providing the documentation needed to demonstrate accountability under GDPR.
Conclusion
Data encryption isn’t just a technical safeguard – it’s a legal requirement and a cornerstone of privacy compliance. According to UK GDPR Article 32, organizations must adopt suitable technical measures to secure data, and encryption is one of the most effective tools available for this purpose [2]. Whether you’re handling sensitive healthcare records under HIPAA or protecting consumer data under CCPA, encryption serves to safeguard both your business operations and the individuals whose data you manage.
Consider the 2020 case of Marriott International Inc., which faced an £18.4 million fine from the ICO for inadequate security measures. The Information Commissioner’s Office has made it clear: “You may face regulatory action… if you don’t implement appropriate technical and organisational measures, such as encryption” [1][2]. This highlights the critical role encryption plays in avoiding penalties and maintaining compliance.
That said, encryption alone isn’t a silver bullet. A comprehensive defense strategy should also include AES-256 encryption, secure key management, multi-factor authentication, and blockchain verification. Tools like ScoreDetect take this further by integrating blockchain checksums, invisible watermarking, and automated workflows alongside traditional encryption methods. As compliance regulations continue to shift, keeping your encryption practices updated is essential.
Staying ahead means more than just adopting encryption – it requires a proactive approach. Using FIPS-approved algorithms, implementing HTTPS across every page, and securing all portable devices with full-disk encryption are steps that ensure your organization is prepared for evolving standards.
To maintain compliance, establish a formal encryption policy, conduct regular DPIAs, and consistently review cryptographic standards. These steps build on the encryption strategies and legal requirements discussed throughout this guide. ScoreDetect’s Enterprise plan simplifies this process with 24/7 monitoring, automated takedowns, and the documentation necessary for GDPR accountability. By combining strong encryption with persistent ownership tracking, your organization can meet current demands while staying ready for future regulatory changes.
FAQs
How does encryption help businesses comply with privacy laws like GDPR, CCPA, and HIPAA?
Encryption is a key tool for businesses aiming to meet privacy law requirements while protecting sensitive data. For instance, under the GDPR, organizations must implement technical measures like encryption to safeguard personal data, ensuring its confidentiality and minimizing the risk of breaches. Similarly, the CCPA calls for "reasonable security practices", with encryption being a widely accepted approach to meet this standard. In the case of HIPAA, encryption is considered an "addressable" safeguard, offering essential protection for electronic health information.
By encrypting data both at rest and during transmission, businesses can not only comply with these regulations but also lower risks and potential liabilities. Effective encryption shields data from unauthorized access and helps ensure that personal and sensitive information remains secure, meeting legal standards along the way.
What are the best practices for managing encryption keys to ensure data security and compliance with privacy laws?
Effective encryption key management plays a critical role in protecting sensitive data and complying with privacy laws like GDPR and U.S. regulations. The first step is to create a clear key management policy. This policy should outline who is authorized to generate, access, and retire keys, while ensuring employees are properly trained on these protocols. Always rely on strong, widely recognized algorithms such as AES-256 for symmetric encryption or RSA-3072 for asymmetric encryption, and steer clear of custom cryptography solutions.
For better security, store your keys in secure environments like hardware security modules (HSMs) or trusted cloud key vaults, rather than general-purpose servers. Access control is equally important – enforce the principle of least privilege, separate key management from usage, and require multi-factor authentication for added protection. Make it a habit to rotate keys regularly, either annually or after a security event, and immediately revoke any keys that have been compromised. Detailed activity logs are essential – track all key-related actions and review these logs periodically to detect any unauthorized access.
Additionally, back up your keys in encrypted, offline storage located in a separate physical location, and routinely test your recovery procedures to ensure they work as intended. Stay proactive by continuously reviewing and refining your key management practices to address emerging threats and keep up with evolving standards.
How can businesses ensure their third-party vendors comply with encryption standards?
To make sure third-party vendors align with your encryption standards, start by setting crystal-clear, contract-defined requirements. These should specify the use of modern encryption algorithms like AES-256 and include best practices, such as regular key rotation and secure key management. Contracts should also grant audit rights, establish reporting schedules, and require documented proof of compliance – think encryption certificates or independent assessments.
Before bringing a vendor on board, take a deep dive into their encryption practices. Check how they stay ahead of emerging threats and confirm they comply with legal frameworks like GDPR or CCPA. Regular audits and monitoring tools are essential for spotting and addressing any compliance gaps.
Tools such as ScoreDetect can simplify this process. By capturing cryptographic checksums of encrypted content and storing them on a blockchain, it ensures tamper-proof evidence. Plus, it generates detailed reports, offering real-time insights into vendor compliance and creating a dependable audit trail for regulatory needs.

