Digital content faces constant risks like theft, piracy, and misuse. Watermark detection offers a solution by embedding invisible markers into digital files – images, videos, audio, and documents – that trace their origin and ownership, even after modifications. This technology helps businesses combat piracy, protect intellectual property, and take action against unauthorized use.
Key Points:
- Invisible Watermarks: Embedded without altering the content’s appearance, they remain detectable after changes like cropping or compression.
- How It Works: Watermarks are inserted during creation and later detected using specialized algorithms to confirm authenticity.
- Applications: Used across industries – media, e-commerce, research, and more – to safeguard assets and prevent misuse.
- Technologies Involved: Frequency-domain methods, steganography, cryptography, and AI-driven detection ensure resilience against tampering.
- Real-World Use: Tools like ScoreDetect combine watermarking with automated web monitoring and takedown processes to enforce copyright effectively.
Watermark detection is an essential tool for protecting digital assets in today’s online landscape.
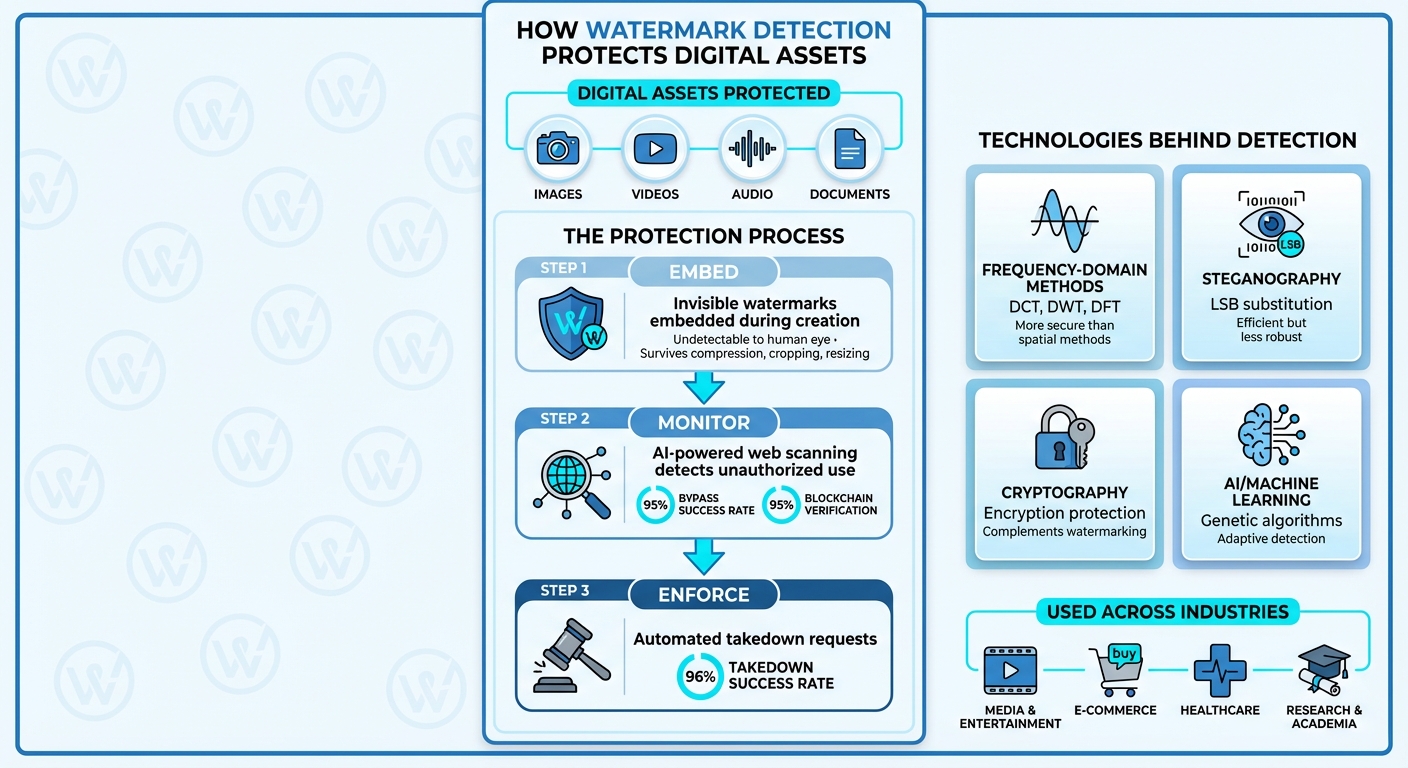
How Watermark Detection Works: From Embedding to Enforcement
Invisible Watermarking: Content Provenance for Videos at Scale | Wes Castro, Meta
sbb-itb-738ac1e
Technologies Used in Watermark Detection
Watermark detection employs a variety of technical approaches, each designed to meet specific content and security requirements. These methods build on the fundamental steps of embedding and extraction, offering tailored solutions for different scenarios.
Frequency-Domain Methods
Frequency-domain techniques focus on embedding watermarks within the frequency components of digital content. Methods like the Discrete Cosine Transform (DCT), Discrete Wavelet Transform (DWT), and Discrete Fourier Transform (DFT) transform content into coefficients, embedding the watermark without directly altering pixel data.
"The frequency-domain digital watermarking algorithms offer significantly more security than their spatial counterparts."
- Rani Kumari and Abhijit Mustafi, Department of Computer Science, Birla Institute of Technology [1]
Advanced methods, such as the Fractional Fourier Transform (FrFT), take this further by dispersing the watermark across both spatial and frequency domains. This added complexity – controlled by the order α – makes the watermark more resistant to attacks. For example, when α = 1, the method behaves like a standard Fourier transform, while α = 0 corresponds to the spatial domain. Moreover, Blind Source Separation (BSS) techniques allow watermark extraction from frequency-domain signals without prior knowledge of the original content or embedding process [1].
Steganographic and Cryptographic Methods
Steganographic methods, often operating in the spatial domain, embed watermarks by modifying pixel intensity values. A common approach is Least Significant Bit (LSB) substitution, where information is hidden in the least significant bits of pixel values. These methods are computationally efficient and can carry large amounts of data. However, they are less robust, as standard image processing techniques can easily remove the watermark [1].
Cryptographic methods, on the other hand, protect digital content by encrypting it during distribution. However, their effectiveness is limited once the content is decrypted.
"Cryptographic systems are quite capable of preventing abuse of digital entities during the distribution phase but are not very effective once the decryption process has been performed."
- Rani Kumari and Abhijit Mustafi, Department of Computer Science, Birla Institute of Technology [1]
Watermarking complements cryptography by providing continuous verification of the content’s origin, even after decryption.
AI and Machine Learning Detection
Artificial intelligence and machine learning have significantly improved watermark detection capabilities. For example, Genetic Algorithms (GA) optimize watermark embedding, ensuring that watermarks remain invisible while maintaining their resistance to tampering. Machine learning models also analyze frequency spectra to detect markers, even after the content has undergone modifications such as cropping, filtering, or re-encoding. These adaptive systems ensure that watermark detection stays ahead of evolving attack techniques [1].
Watermark Detection for Different Media Types
Watermark detection isn’t a one-size-fits-all process. Each media type – images, text, audio, and video – comes with its own set of challenges. Images face issues like distortion, text is vulnerable to editing, and audio or video must withstand compression and piracy attempts. Tailoring detection methods to these unique needs is essential.
Images and Graphics
Images and graphics are often targets of geometric attacks like rotation, scaling, and cropping. These distortions can disrupt synchronization, making it harder to detect watermarks. Additionally, JPEG compression can completely wipe out embedded watermark data [2][3].
To counter these threats, techniques like transform domain methods (DCT, DWT, SVD) and feature-based synchronization tools (e.g., Harris-Laplace detectors) are used to improve watermark durability against distortions [2][3].
"The value of watermarking comes from the fact that regular sideband data may be lost or modified when the digital signal is converted between formats, but the samples of the digital signal are (typically) unchanged."
- Zhe-Ming Lu and Shi-Ze Guo [3]
In fields like healthcare, watermarking must be lossless or reversible. Even tiny changes in pixel values can affect medical diagnoses, making standard watermarking unsuitable for such critical applications [3].
Text documents, however, require an entirely different approach to address their specific vulnerabilities.
Text and Documents
Text-based content presents its own challenges. Tools like screen capture and editing software can easily bypass traditional watermarks. The key is finding a balance between security and readability – watermarks must protect the content without interfering with its usability [4].
Dynamic watermarking offers a solution by embedding real-time user data such as IP addresses, usernames, and timestamps. This approach links each document view to a specific individual, creating accountability. For highly sensitive materials like classified documents or unpublished research, repetitive diagonal watermarks covering the entire page make partial editing or cropping much harder [4].
Placement also matters. Centered watermarks are ideal for security-focused documents to prevent cropping, while corner placements work better for branding purposes where usability is more important [4].
Audio and video content, on the other hand, require techniques that address compression and piracy.
Audio and Video Content
Protecting audio and video content involves embedding watermarks that remain intact even after compression or collusion attacks.
For audio, this often means modulating hidden tones or frequencies that survive standard compression algorithms. Video uses forensic watermarking, embedding metadata like IP addresses and timestamps to trace piracy or leaks. This is especially important for streaming platforms and content distributors who need to track unauthorized copies [2].
A newer approach involves multimodal embedding, where one type of media (like audio or video) is hidden within another, such as an image, using advanced techniques like 3D-CNNs and LSTM models. This method enhances protection for high-value content [3].
What Makes a Good Watermark Detection System
Picking the right watermark detection system isn’t just about adding protection – it’s about ensuring reliable and scalable performance that meets your needs. The best systems combine precision, seamless integration, and advanced features that can handle real-world challenges.
Accuracy and Resistance to Modifications
A strong watermark detection system must hold up against real-world alterations. Think about how often your content gets compressed, cropped, resized, or has noise added – especially on platforms like social media where files are processed automatically. Even after these changes, the system should still deliver high detection accuracy [7].
Watermark detection operates like a hypothesis test (H₀: watermark present, H₁: absent), and minimizing false positives is critical. Even a low false-positive rate can lead to significant errors when dealing with large volumes of assets [3].
"Performance and Scalability Are Non-Negotiable. If you handle large volumes of content, performance matters. Watermarking and detection must happen in real time, without bottlenecks."
Before you commit to a system, it’s smart to test it with assets that have undergone the same kinds of alterations your content typically faces. This ensures the system performs well under conditions similar to your actual workflow [6][7]. Reliable performance also depends on how well the system integrates with your existing tools and processes.
Integration and Scalability
A good detection system should fit smoothly into your current setup without requiring expensive changes. Look for systems with well-documented APIs and sandbox environments so your developers can test integration speed and compatibility before rolling it out [7]. It should also work seamlessly with your CMS, DAM platforms, and editing tools [7].
Efficiency is key, especially as your workload grows. For example, Meta Engineering created a CPU-based video watermarking solution that achieved end-to-end latency within 5% of GPU-based systems while being more cost-effective [6]. Similarly, Google DeepMind‘s SynthID-Text proved its scalability by handling nearly 20 million Gemini responses in a live test [5].
"With proper optimizations, CPU-only pipelines can reach performances comparable to GPU pipelines for specific use cases at much lower cost."
- Meta Engineering [6]
Pay close attention to latency – the extra time watermarking and detection add to your workflow. A high-performance system should process thousands of assets daily without slowing you down [5][7]. For video content, assess the BD-Rate impact, as initial implementations can increase bitrate by about 20% before optimizations [6].
You should also consider deployment flexibility. Cloud-based (SaaS) solutions offer quick setup, while on-premise options give you more control over sensitive data [7]. Choose the setup that best matches your infrastructure and security needs.
On top of performance, advanced features can take your protection to the next level.
Advanced Protection Features
Today’s watermark detection systems do more than just embed and detect watermarks. Real-time monitoring can flag unauthorized usage as it happens, while automated alerts notify you the moment protected content appears on unapproved platforms, allowing for a quick response.
Features like batch processing and automated triggers simplify operations by applying protection automatically as your content moves through production [7]. These tools save time and ensure your assets, including educational content, are consistently protected.
How ScoreDetect Protects Digital Assets
ScoreDetect offers a streamlined solution for safeguarding digital assets, combining watermark embedding, monitoring, and enforcement into one powerful tool. By integrating invisible watermarking technology with advanced AI, it handles every step – from embedding watermarks to tracking improper use and initiating automated takedown requests. Here’s a breakdown of how ScoreDetect ensures comprehensive protection.
Invisible Watermarking Technology
ScoreDetect uses invisible watermarks to tag your digital assets without altering their quality or appearance. These digital markers are undetectable to the human eye and are designed to endure common modifications like compression, cropping, or resizing. Whether it’s images, videos, audio files, or documents, this AI-powered technology ensures your assets remain protected.
The embedded watermarks are built to withstand transformations while staying verifiable. To add an extra layer of security, blockchain-recorded checksums provide tamper-proof proof of ownership, eliminating the need to store the actual files.
Content Discovery and Verification
Once assets are watermarked, ScoreDetect’s discovery engine actively scans the web for unauthorized use. Using targeted web scraping with a 95% bypass success rate, it identifies potential infringements. The tool then compares the discovered content with the originals, using quantitative methods like checksums and blockchain hashes to confirm violations.
Automated Takedown Process
When unauthorized use is confirmed, ScoreDetect takes swift action. It automatically generates takedown requests tailored to meet compliance standards, ensuring hosting providers can act quickly. With a verified watermark match, the system achieves an impressive takedown success rate of over 96%, helping protect your assets efficiently and effectively.
Conclusion
Key Takeaways
Watermark detection works by embedding invisible markers into digital content, offering a way to prove ownership and deter piracy – even if the content is modified. These watermarks are designed to survive alterations while staying undetectable to the naked eye.
The primary advantage of this technology is its ability to provide solid proof of ownership and combat unauthorized use. Industries like media and entertainment use it to fight piracy, e-commerce businesses protect product images, and academics safeguard their research. For example, ScoreDetect boasts a 95% success rate in identifying unauthorized content and achieves over a 96% takedown rate. Additionally, blockchain checksums add an extra layer of tamper-proof copyright protection.
Next Steps for Businesses
If your business produces or manages digital content, watermark detection should be on your radar. Start by identifying your most vulnerable assets and consider adopting a solution like ScoreDetect. Its features include automatic, invisible tagging, quick content discovery, and fast takedown of infringements.
Choose a watermarking tool tailored to your industry needs, integrate it into your existing platforms, and keep a close watch for unauthorized use. Investing in this technology reduces piracy risks, strengthens copyright enforcement, and builds trust with your audience.
FAQs
How can invisible watermarks still be detected after content is altered?
Invisible watermarks are crafted to stay detectable, even after typical content modifications such as compression, resizing, or the addition of noise. These watermarks are embedded within the content’s spatial or frequency domain, making them tough to remove or distort.
With the help of advanced AI-driven techniques, their durability is further improved. These techniques allow the watermark to adjust to different types of edits, ensuring that even after major changes, the embedded markers remain identifiable. This provides dependable protection for digital assets.
How does watermark detection work to protect different types of digital media?
Watermark detection employs cutting-edge methods to protect digital media like images, videos, and audio. Invisible watermarking algorithms play a key role by embedding subtle markers into content that are undetectable to the naked eye but remain intact even after alterations like compression or resizing. Techniques such as Discrete Wavelet Transform (DWT) and Discrete Cosine Transform (DCT) are often utilized to ensure these watermarks are durable and resistant to tampering.
For audio and video content, approaches like spread spectrum and statistical watermarking scatter the watermark across the file, making it much harder to erase. On top of that, AI-driven detection systems excel at identifying watermarks in media that has undergone significant changes or is highly complex. Some systems even integrate blockchain technology to generate cryptographic checksums, providing verifiable ownership proof without needing to store the original files. Combined, these technologies offer strong safeguards for digital assets across different formats.
How does ScoreDetect protect digital assets and prevent misuse?
ScoreDetect safeguards your digital assets by embedding invisible, tamper-resistant watermarks directly into your content. These watermarks are built to withstand changes like compression, resizing, or cropping, making them extremely difficult for anyone to remove. This ensures you can accurately track and identify any leaked or misused materials.
The platform also leverages blockchain technology to generate a checksum for your content, offering undeniable proof of ownership without needing to store the files themselves. On top of that, ScoreDetect provides tools for automated monitoring, detecting unauthorized use, and initiating swift takedown actions – keeping your assets secure and under your control.